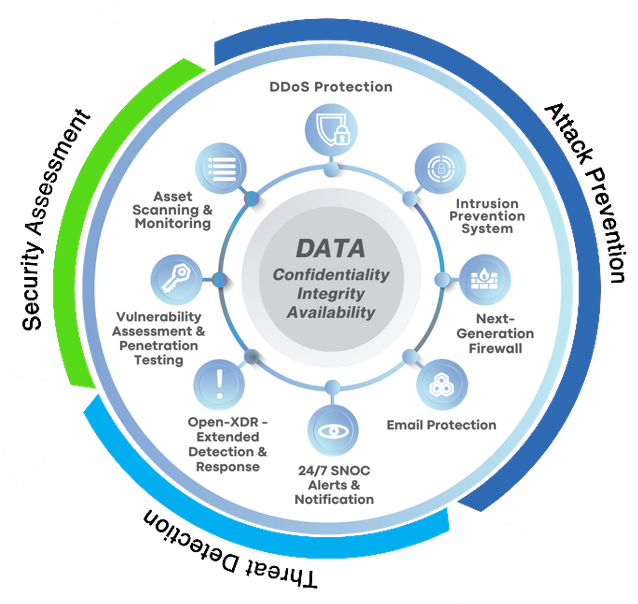
Stay Ahead of Cyber Threats
Proactively protect your organization’s public-facing infrastructure with Continuous Threat Exposure Management (CTEM). Our service ensures early detection of vulnerabilities and provides actionable insights to maintain a robust security posture.
What is Continuous Threat Exposure Management?
Continuous Threat Exposure Management (CTEM) is a proactive cybersecurity approach designed to help organizations identify, assess, and remediate vulnerabilities in their public-facing infrastructure. By leveraging automated tools and regular assessments, CTEM minimizes the risk of cyber threats and ensures your business stays secure.
Key Features of CTEM
- Comprehensive Coverage: Scheduled port scans, vulnerability assessments, and penetration testing (VAPT) on Internet-facing infrastructure.
- Advanced Tools: Powered by Ridge Security for thorough scanning and reporting.
- Regular Assessments: Monthly or quarterly evaluations tailored to your security needs.
- Detailed Reporting: Monthly reports with executive summaries, business risks, open ports, and vulnerability trends.
Benefits of CTEM
- Continuous Detection: Monitor for changes in network configurations, weak protocols, and public-facing vulnerabilities.
- Early Remediation: Address threats as soon as they are identified to minimize risks.
- Trend Analysis: Gain insights into security improvements with monthly differential reports.
CTEM vs. External VAPT
| Aspect | CTEM | External VAPT |
|---|---|---|
| Scope | Internet-facing IP addresses only (e.g., servers, websites, network devices). | Internet-facing IP addresses and web applications. |
| Frequency | Scheduled monthly or quarterly (1-year contract). | One-time, based on the client’s schedule. |
| Effort Estimate | Low – Managed Security Services (MSS). | High – Professional Security Services (PSS). |
| Tools | Automated VAPT using Ridge Security. | Manual testing with open-source and paid tools. |
| Reporting | Standard Ridge Security report with Netpluz cover page. | Customized Netpluz VAPT format. |
| Meetings | None (report delivered directly to the customer). | Includes exit meeting (onsite or online). |
| Customer Value | Frequent testing for continuous security. | In-depth coverage and detailed insights. |
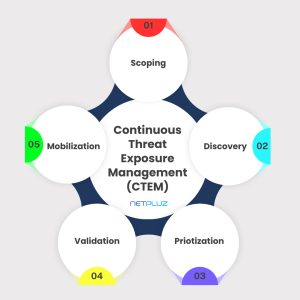
The Five Stages of a CTEM Program
-
- Scoping: Define the assessment boundaries and objectives.
- Discovery: Identify all Internet-facing assets.
- Prioritization: Rank vulnerabilities by risk level.
- Validation: Confirm vulnerabilities and their impact.
- Mobilization: Implement remediation strategies.
Ready to Enhance Your Cybersecurity?
Protect your organization with Netpluz’s Continuous Threat Exposure Management service.
Contact us today to schedule a demo or learn more about how CTEM can bolster your cybersecurity defenses.