We are thrilled to announce the opening of our brand-new regional office in Hong Kong, furthering our commitment to providing top-notch cybersecurity services!
As cyber threats continue to evolve and businesses face increasing challenges in securing their digital assets, our expansion in Hong Kong enables us to offer localized and robust cybersecurity solutions to businesses in the region.
With the establishment of our new office, our commitment intensifies in aiding organizations within Hong Kong, as well as those with a multi-presence in the region, to fortify their defenses against cyber threats and safeguard their invaluable data. Our seasoned team of cybersecurity experts stands ready to deliver a comprehensive suite of services, encompassing threat intelligence, vulnerability assessments, incident response and managed security solutions.
Netpluz’s focus on cybersecurity allows us to stay ahead of emerging threats and offer cutting-edge solutions tailored to our clients’ specific needs. By opening this regional office in Hong Kong, we aim to forge strong partnerships and work closely with local businesses to ensure their digital security.
We’re proud to extend our presence to Hong Kong, adding to our established locations in Singapore, Malaysia, Thailand, and the Philippines. Together, we will strengthen the cybersecurity landscape and create a safer digital environment for businesses to thrive.
It never rains but it pours. Your data just got stolen, and the next thing you know, you’re facing a $16,000 fine. That’s why it’s crucial that data breaches do not happen and you should be aware of how you can protect your company with cyber security hand-in-hand with Personal Data Protection Act (PDPA) Compliance.
A data breach is a security incident in which information is accessed without authorisation. It usually happens when there is an unauthorised entry point into an organisation’s database that allows hackers to access customer data such as passwords, credit card numbers, banking information and other sensitive information.
Data breaches can hurt businesses and consumers in a variety of ways. They are a costly expense that can damage lives and reputation.1
What is the Personal Data Protection Act (PDPA)?
The PDPA is an act enforced by the Personal Data Protection Commission (PDPC). It is a data protection law that comprises various rules governing the collection, use, disclosure and care of personal data. It identifies both the rights of individuals to protect their personal data and the needs of organizations to collect, use or disclose personal data.2
10 questions to ponder if your company complies with the PDPA3
- Do you have a Data Protection Officer?
All organisations must appoint at least one person as the Data Protection Officer (DPO).
The DPO function is management’s responsibility and, ideally, the appointed DPO should be part of the management team. The operational DPO functions, however, may be delegated to one or a few employees, or outsourced to a service provider (Data Protection Service Provider).
Once you have decided on the person(s) to appoint, it is important to brief him/her on his/her roles and responsibilities. Next step is to inform all your staff on who the DPO is so that they can forward all PDPA-related queries and feedback to him/her.
- Do you notify the customer of your purpose in collecting, using or disclosing his/her personal data?
The customer should be fully aware of what and why their personal data is collected/used/disclosed for.
- Do you seek the customer’s consent when collecting, using or disclosing his/her personal data?
The customer should give their consent when their data is used, collected or disclosed.
- Do you allow the customer to withdraw consent at any time when collecting, using or disclosing his/her personal data?
The customer should be allowed to withdraw consent at any time regarding their Personal data.
- Do you have an adequate response (within 30 days) when individuals ask about how their personal data has been used?
If you are unable to provide it within 30 days, you must inform the individual within 30 days and let him/her know when you can respond.
- Do you allow the correction of Personal data?
Are customers allowed to correct or update their data maintained by the organisation?
- Are security arrangements in place to protect all personal data under your organisation?
Establish security arrangements to protect personal data under your organisation. This is to prevent unauthorised access, collection, use or disclosure of the data and other similar risks.
- Did you dispose of personal data that is no longer needed?
Stop holding on to personal data when you no longer have any business or legal use for it.
- Did you check the Do Not Call Registry before doing telemarketing?
If you conduct telemarketing to subscribers or users of Singapore telephone numbers, you will need to submit the telephone numbers on your telemarketing list for checks against the Do Not Call (DNC) Registry, unless the subscriber or user has given his/her clear and unambiguous consent to receive such messages.
- Communicate your data protection policies, practices and processes
Provide the business contact information of your DPO so that your customers can contact him/her for PDPA-related queries or complaints
How does Cyber Security help to mitigate the risk of data breach?
A data breach is very much avoidable with the correct measures in place.
It is not wise for organisations to skimp on cyber security expenses. In this age when data is so valuable, a breach has certain irreversible consequences.
Ways to mitigate the risk of data breach with cyber security
- Critical Infrastructure Security
Cyber security helps in securing your IT infrastructure as a whole which secures any mission critical applications that cannot afford any downtime.
Common attacks such as DDoS, can be prevented with adequate firewall in place to detect any incoming attacks through a mitigation facility. Through this method, customers’ IP addresses are masked with a Virtual IP so that all data traffic will be redirected before it reaches their network. 4
- IP Address
Usually, an organisation may have a server with an externally facing IP, exposed to the internet, within a DMZ. These servers have static IP addresses which are accessible from anywhere with an Internet connection.
It is consequential for organisations to ensure this public address range is frequently scanned for exploits and weaknesses to ensure that crucial data is not leaked.
One method to mitigate this is to use application layer defenses, consult a network firewall provider that has strong application layer protection. A firewall should have the ability to inspect the content of traffic and block malicious requests. Another method of mitigation can be by having a dynamic IP address that changes over time and is different each time you connect to the internet. Dynamic IP address reduces the chance of IP address hacking as it is changing over time and is difficult for hackers to decode. 5
- Cloud Services
Is the convenience of the Internet still as enticing after knowing the threats? Fret not! Put in place your cloud security to mitigate the risk of data breach when storing your data in the cloud!
Insufficient due diligence will cost you greatly, hire the right people to monitor what’s going on in your workspaces can help you avoid or hold back data breaches or you can consult a unified cloud management platform. 6
Conclusion
All in all, cyber threats are imminent and impending, the PDPA is a very important legislature in data handling and exchange. Hackers will continue to mine the cyberspace for any information that they can exploit financially and it is important to be ready when the push comes to shove.
Netpluz can be your one stop solution for all cyber security services that your company might require. Our managed cyber security services include cloud based simple and cost effective solution to mitigate and protect against any external threats, such as D-DOS attacks, secures any backend network and mission critical applications that cannot afford any downtime.
Please feel free to book an appointment by submitting your information here for a free consultation.
Author: Ong Wei Zhao
References
2 https://www.pdpc.gov.sg/Legislation-and-Guidelines/Personal-Data-Protection-Act-Overview
4 https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/
5 https://www.sciencedirect.com/topics/computer-science/internal-server
6 https://medium.com/swlh/7-ways-to-secure-your-office-365-from-data-breach-86537dcb70db

According to the National Cyber Security Alliance, over 70% of cyber attacks target small businesses, and 60% of the companies that got hacked can go out of business after 6 months. [1] With poor cybersecurity, a business, regardless of size, may suffer from losses or even cease operations. Businesses should be more aware of the consequences of poor cybersecurity given the high frequency of cyber-attacks and at the same time, stay informed on the preventive measures.
How can poor cybersecurity harm businesses? [2] [3] [4]
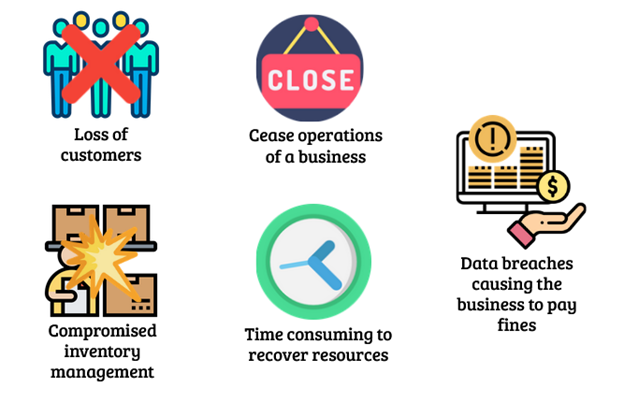
1.Loss of customers
When data breaches happen, the news may spread and the company’s reputation will be tarnished. According to Gemalto, 70% of customers will stop dealing with the company after a data breach. Naturally, loss in customers leads to a loss in revenues and profits.
2. Compromised inventory management
Cybersecurity may damage the company’s inventory management. Once damaged, the company may face difficulties in recovering back lost information. Inventory management is important for keeping track of orders from suppliers and the products customers usually buy and the channels of purchase. Poor cybersecurity may lead to a detrimental disruption in the company’s operations.
3. Cease operations of a business
According to Accenture, cyber attacks have cost businesses $5.2 trillion worldwide in 5 years. Moreover, when the company’s IT infrastructure gets compromised, it might take time to recover it and some businesses need their technologies such as accessing customer data to continue their business. Therefore, if a cyber attack happens the company might have to cease operations which might lead to lost customers.
4. Time-consuming to recover resources
The process to restore data and operations and data after a cyber attack is also very time-consuming. Businesses may have to halt operations during the recovery process, thereby impacting the growth of the business when management shifts its focus on data recovery.
5. Data breaches causing the business to pay fines
With the severity of data breaches, these may result in legal fines being imposed on the company. Apart from implementing cybersecurity, companies have to adhere to the Personal Data Protection Act (PDPA) requiring the maintenance of customer data privacy and confidentiality. Penalties for data breaches could be in the millions of dollars. One example of a company that got penalised for data breaches is British Airways. In 2018, British Airways faced a data breach incident which led to a penalty of about $230 million.
What can you do to prevent cyber attacks? [5] [6]
Now that you know how poor security could affect your business, here are some ways to prevent cyber attacks from happening to your company.
1. Encrypt and backup data
One of the most effective ways to prevent data breaches is to encrypt your data. Data encryption allows the data to be unreadable and it can only be decoded with the right key. This helps to protect the data or making the data harder to decode when a cyber-attack happens. Another way to prevent data breaches is by frequent data backups. If ransomware happens to the company and the hacker is asking for a ransom to decrypt the data, you do not have to worry as your data is already backed up somewhere else.
2. Do not use a simple password
One of the most basic cyber-attack preventions is to use a complicated and strong password. The password should not be shared easily and only appropriate users will know the password. The password set should not be written down on paper or anywhere accessible as you might not know if an attacker will intrude and seize any sensitive information.
3. Invest in cybersecurity insurance
In 2019, the Personal Data Protection Commission (PDPC) issued over $12.9 million in fines to companies in Singapore that have broken the Personal Data Protection Act (PDPA).[3] The SingHealth cyber-attack that caused 1.5 million patient records to be stolen was fined $250,000 and Integrated Health Information Systems (IHiS) was fined $750,000. Therefore, it is important to invest in cybersecurity insurance as insurance helps to reduce the losses when a cyber-attack hit a company.

Source: ST FILE
4. Train your employees to minimise the risk of cybersecurity
One of the most important steps to prevent cyber attacks is to train your employees on the rules and regulations they should take to minimise the risk of cyber-attacks. For example, reminding staff to change their passwords frequently or not to open suspicious-looking emails. One small and wrong step from the employees could lead to a successful cyber attack.
5. Hire cybersecurity experts
Lastly, hire an external cybersecurity expert to do testing on your company’s security and help you to access the risk of your company getting a cyber attack. The expert can also advise you on how to prevent cyber attacks.
Conclusion
Do you still think that poor cybersecurity will not cause a big effect on your business – in terms of financial losses, lost customers, effort to recover resources or, even the risk of bankruptcy! This can be prevented with a few steps such as using data encryption, frequent data backup, use of complicated passwords, investing in cybersecurity insurance, training employees, and hiring cybersecurity experts.
Want to find out more about cybersecurity and how to take measures to prevent cyber-attacks? Click here to find out more. Netpluz has partnered with various reliable cybersecurity giants such as Sophos and Nexusguard to provide your ideal cybersecurity service. To book a free appointment with us, please input your information here. For additional enquiries, you can contact us here.
Author: Tan Hui Xuan Coco Vanna
References
- Koulopoulos, Thomas. “60 Percent of Companies Fail in 6 Months Because of This (It’s Not What You Think).” Inc.com, Inc., 11 May 2017, www.inc.com/thomas-koulopoulos/the-biggest-risk-to-your-business-cant-be-eliminated-heres-how-you-can-survive-i.html
- Matthews, Kayla, et al. “6 Ways Poor Cybersecurity Hurts Businesses.” Security Boulevard, 17 May 2019, securityboulevard.com/2019/05/6-ways-poor-cybersecurity-hurts-businesses/
- Ashe-Edmunds, Sam. “Consequences of Poor Security in a Company.” Small Business – Chron.com, Chron.com, 21 Nov. 2017, smallbusiness.chron.com/consequences-poor-security-company-70227.html
- “The Cost of Cyber Attacks to Businesses.” Horangi, www.horangi.com/blog/the-cost-of-cyber-attacks-to-businesses/
- Goud, Naveen, et al. “Ways to Prevent Cyber Attacks on Your Company.” Cybersecurity Insiders, 19 July 2018, www.cybersecurity-insiders.com/ways-to-prevent-cyber-attacks-on-your-company/
- Popat, Alniz. “Five Ways To Protect Your Company Against Cyber Attacks.” Entrepreneur, 19 July 2018, www.entrepreneur.com/article/316886
A Chess Game With Cyber Criminals
Managing cybersecurity in a business is like a chess game with cyber criminals. There is a lot to think about and one wrong move could result in a checkmate.
As the world gets more connected, it also brings more opportunities for these criminals to engage in their activities in the digital world.
Singapore is known to be one of the safest countries in the world but how safe are we exactly in the digital world?

According to the Cyber Security Agency of Singapore (CSA), its 2019 Singapore Cyber Landscape Report indicated an increase in the number of cyber threats. Some of these common cyber threats include website defacement incidents, phishing and malware infections. For website defacements, there was an increase from 605 cases in 2018 to 873 cases in 2019. Majority of the attacks were targeted at SMEs. For phishing and malware infections, CSA reported attack origins from mostly Singapore.
This is an alarming trend, as SMEs, unlike big corporations, may not necessarily have the deep pockets in employing high-end cybersecurity solutions. In addition, with the recent changes to the Personal Data Protection Act (PDPA) in Singapore, businesses are expected to pay a heavier fine in the event of a data breach.
According to Synergix Technologies, SMEs contribute 50% of Singapore’s national GDP. In other words, if SMEs were to crumble, so will Singapore’s economy. This shows the importance of SMEs in Singapore and the urgency of those cyber threats being neutralised.
Many SMEs may already have some common cybersecurity solutions in place such as Firewall Protection, Endpoint Protection and Anti-Virus/Spam. These are the fundamentals any SMEs should have, however, staying ahead of the game would mean going beyond.
So how exactly do I stay ahead?
Recognise that it is like a game of chess. Staying ahead would require multiple strategies devised to predict movements and protect your important chess pieces.

You Are Your Own Worst Enemy.
In a game of chess, a single bad move could lead to your opponent’s victory. Similarly, a single click from an employee could lead to a possible cyber attack. In most cases, cyber criminals get their way due to employees’ negligence. Human error was identified as the root cause for 8 in 10 cyber attacks during the pandemic period. With working from home becoming the new norm, it is difficult for businesses to keep track of what their employees are clicking on or downloading. This usually happens among the lower-level employees suggesting a strong need for monitoring. However, it can be remedied if employees were to be given ample training on cyber security awareness. With these training sessions, employees can then adopt healthier working habits online, thus denying cyber criminals possible gateways to the organisation.
Know Thy Enemy.

You now know your worst enemy, what about your common enemies? There are a few common cyber threats that businesses should know about; they include malware, phishing emails, zero-day exploits, denial-of-service-attack and many more that one can fall to. Employing a third-party service provider is the best solution for businesses as they have a comprehensive team of experts that can help manage their cybersecurity needs. They know best. Furthermore, hiring highly experienced IT professionals may not be the most cost-efficient compared to a managed service provider in the long run.
Checkmate.
The one move that says it all. There are so many different approaches to a game of chess. What if I told you they can be simplified into just one? One move, one solution.

To simplify and satisfy communication needs, Netpluz offers a comprehensive solution for businesses called the eSentinel. The eSentinel is a 360-degree one-stop cybersecurity platform simplified for businesses that covers the main three aspects of cybersecurity, attack prevention, security assessment and threat detection. Its main features include DDoS Mitigation for the External Defense Layer, Next-Generation Firewall, Intrusion Prevention System, 24/7 SNOC Monitoring with alerts & notification, Customisable Network-layer policies and Periodic Vulnerability Assessment for the Internal Defense Layer. These features were only for bigger corporations with deep pockets originally but with eSentinel, Netpluz is now able to provide more quality services to SMEs at an affordable rate.
This is a game-changing solution in the market especially for SMEs that are looking for a well-rounded solution that would not burn a hole in their pockets.
Conclusion
With all the good practices and solutions in place, it would not be easy for cyber criminals to act upon your business. However, the human error factor is still rather unpredictable. With all the preventive measures in place, providing training and monitoring on employees, it is still possible that a cyber attack might happen.
In situations like these, cyber insurance can be very useful for SMEs to cushion their financial impacts in an event of a cyber attack, leading to data breaches. For an email phishing incident, cyber insurance covers the full cost of the forensics process and for ransomware incidents, it covers the full cost of bitcoins as they are usually the currency requested to be paid in.
To learn more about cyber insurance and eSentinel’s extensive palette of security features, do sign up for the upcoming webinar by Netpluz, featuring Commercial Director, Kenneth Wee and guest speaker from Chubb, Elsa Xu, Financial Lines Manager. The webinar, “Cyber Risk Management in the New Digitalisation Age” will highlight the features of how cyber insurance and eSentinel plays a part in today’s digital world with risk management processes.
References:
“Cyber Threats Grew in 2019 Amid Rapidly Evolving Global Cyber Landscape.” Cyber Security Agency, www.csa.gov.sg/news/press-releases/cyber-threats-grew-in-2019-amid-rapidly-evolving-global-cyber-landscape#:~:text=Cybercrime%20remains%20a%20concern.
Bianculli, Larry. “10 Common IT Security Risks in the Workplace.” CCSI, 10 Oct. 2017, www.ccsinet.com/blog/common-security-risks-workplace/.
“Business Challenges for SMEs in Singapore in 2019.” Synergix Technologies ERP System, www.synergixtech.com/news-event/business-blog/business-challenges-smes-2019/#:~:text=In%20Singapore%20currently%2C%20there%20are.
Kass, DH. “Research: Human Error, Stress and Cybersecurity Amid COVID-19 Pandemic.” MSSP Alert, 12 Nov. 2020, www.msspalert.com/cybersecurity-research/covid-19-cyber-risks/.
Author: Sebastian Toh
Data Breach – When Traditional Layers Of Cybersecurity Fail
“How Prepared Are You?”
What happens when your traditional layers of cybersecurity fail? How can you stay ahead of the game? Nobody could ever be prepared enough when it comes to cybersecurity. The best that one can do is to expect the worst and be ready to receive the impact when it comes.
The Age of Digitalisation brought much success to many businesses, be it SMEs or big corporations. However, with these success stories, an alarming number of cyber attacks are reported in recent years. These cyber attacks hinder businesses and greatly affect many aspects such as credibility, work efficiency and most importantly loss in revenue. Cyber attacks can come in various forms, examples include malware, phishing emails and more which can lead to possible data breaches.
According to a 2019 survey by endpoint security firm, Carbon Black, 96% of the surveyed Singapore firms have had data breaches due to cyber attacks. The results are worrying as data breaches can impact a business financially to a huge extent. These attacks are estimated to cost Singaporean businesses $1.7million per breach, according to Channel Asia. These numbers can easily cripple and crumble many SMEs that are not financially ready to receive such an impact. In Singapore and Malaysia, SMEs contribute to 40% each for their nation’s GDP, translating that the importance of SMEs in these countries.
With the recent changes to the Personal Data Protection Act (PDPA) in Singapore, businesses that are found guilty of a data breach are now expected to pay a heftier fine based on their annual company turnover. This is to ensure a safer environment in the digitised world by strengthening data protection standards. From SMEs to big corporations, there is always much valuable and personal data that can be potentially compromised. The data may include customer’s personal data as well as employee’s personal data such as NRIC, Date of Birth, residential addresses and bank information. In recent news, Eatigo reported a data breach with potentially 2.8 million accounts illegally accessed. Similarly, Lazada, reported a data breach from their recent acquisition, RedMart. It was reported that personal information from 1.1million RedMart accounts was stolen as a result of the data breach.
If you think that SMEs are safe from cyber attacks, you are wrong. In fact, 43% of cyber attacks were reportedly targeted at SMEs. In 2019, Homegrown fashion label, Love, Bonito reported a data breach with their users’ information compromised. SMEs may not be able to cushion such an impact financially compared to big corporations with deep pockets, especially with the new amendment to the PDPA. For many SMEs, it could mean the closure of businesses. However, there are certain measures that SMEs could implement to prevent being caught in such a situation.
Hire an external consultant
Businesses should always be looking towards increasing productivity and efficiency that translates to revenue. This is why hiring an external consultant or a service provider to manage your data and cybersecurity needs is vital. Businesses shouldn’t be worrying about scouting for cybersecurity talents. Not only are they much more costly, it is also more feasible to let a team of experts who specialise in specific areas of expertise, manage your data and security solutions. In addition, they are well equipped with knowledge and experience which can definitely bring much value in the event of a cyber attack. Hence, there is a business case for engaging MSPs to handle cybersecurity as it is more cost efficient.
Let the experts manage and mitigate cyber risks while your business focus on the main goal of profiting.
Employee Training

You can be well protected in every aspect, thinking there are no loopholes. However, research has shown that more often than not employees unknowingly aid in cyber attacks leading to data breaches. According to Security Magazine, employees are behind 4 in 10 data breaches. Phishing emails and file-based malware are among a few common deceits that employees usually fall for. This suggests a strong need for businesses to provide frequent training on cybersecurity for their employees as they are the weakest link.
The Failsafe
The big question: WHAT IF? When all else fails, what can businesses rely on? Most businesses may already have security measures implemented to prevent cyber attacks however, in the worst case scenario, a data breach might still happen.

Cyber insurance helps businesses cushion their financial impact in the case of a cyber attack and data breach. For example, during an email phishing incident, cyber insurance covers the entire cost of the forensics process which is a huge financial setback for businesses if not insured. In ransomware incidents, bitcoins are usually the currency requested to be paid in. However, if insured, the ransom fee would be covered in full. SMEs can easily crumble if caught in situations like these, paying a huge sum of money for forensics and bitcoins.
Where and How to Get Covered?
Netpluz Asia is the first Managed Communications Service Provider (MSP) to introduce cyber insurance into our existing wide array of comprehensive data, voice and video solutions. As a one-stop MSP with 24/7 support, Netpluz Asia can help spur your businesses on to greater heights while making the journey smooth and secure by the delivery of high quality services.
An upcoming webinar by Netpluz Asia featuring Commercial Director, Kenneth Wee and guest speaker from Chubb, Elsa Xu, Financial Lines Manager, aims to highlight the topic of cybersecurity management, risk transfer and how insurance comes into play.
To find out more about the webinar and cyber insurance click here
References:
Baharudin, Hariz. “Love, Bonito Customers’ Data Breached, Credit Card Details Exposed, Watchdog Investigating.” The Straits Times, 13 Dec. 2019, www.straitstimes.com/tech/love-bonito-customers-data-breached-credit-card-details-exposed-watchdog-investigating.
“Carbon Black Reveals 96 Percent of Firms in Singapore Suffer Data Breaches.” CISO MAG | Cyber Security Magazine, 3 Oct. 2019, cisomag.eccouncil.org/around-96-percent-of-singapore-businesses-suffer-data-breach-survey/#:~:text=Around%2096%20percent%20of%20Singapore%20Businesses%20Suffer%20Data%20Breach%3A%20Survey,-By&text=According%20to%20the%20research%20findings,an%20increase%20in%20attack%20volumes.
“Eatigo Reports Data Breach, Personal Data from Customer Accounts Listed for Sale Online.” CNA, www.channelnewsasia.com/news/singapore/eatigo-data-breach-personal-information-millions-account-13425082.
Henderson, James. “Security Attacks Cost Singaporean Businesses $1.7M per Breach.” Channel Asia, www.channelasia.tech/article/670400/security-attacks-cost-singaporean-businesses-1-7m-per-breach/.
Kapur, Ricky. “Cybersecurity for Small-and-Medium Enterprises in Asia Pacific.” Microsoft Stories Asia, 29 Oct. 2020, news.microsoft.com/apac/2020/10/29/cybersecurity-for-small-and-medium-enterprises-in-asia-pacific/.
“Lazada Suffers Data Breach; Personal Information from 1.1 Million RedMart Accounts for Sale Online.” TODAYonline, www.todayonline.com/singapore/lazada-suffers-data-breach-personal-information-11-million-redmart-accounts-sale-online.
“Microsoft: Digital Transformation Doesn’t Make SMEs Immune to Cyber Threats.” Securitybrief.Asia, securitybrief.asia/story/microsoft-digital-transformation-doesn-t-make-smes-immune-to-cyber-threats.
“Stressed Employees behind 4 in 10 Data Breaches.” Www.Securitymagazine.com, www.securitymagazine.com/articles/93921-stressed-employees-behind-4-in-10-data-breaches.
Wong, Lester. “Parliament: Proposed Changes to PDPA Include Stiffer Fines for Data Breaches, Mandatory Notification When They Occur.” The Straits Times, 5 Oct. 2020, www.straitstimes.com/politics/parliament-proposed-changes-in-law-include-stiffer-fines-for-data-breaches-mandatory.
Author: Sebastian Toh
Choosing the best cloud model for your business
Simply put, cloud computing is the delivery of computing services—including servers, storage, databases, networking, software, analytics, and intelligence—over the Internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale. You typically pay only for cloud services you use, helping lower your operating costs, run your infrastructure more efficiently, and scale as your business needs change. 1
A Tech Pro Research survey revealed that 38% of companies are already using industry cloud services, and 19% plan to do so within the next 12 months, making a solid majority of 57% either using or planning to use industry cloud services. Another 23% of respondents said they are considering it, but they haven’t set a timeline for adoption. This means that only 20% have completely ruled out industry cloud services.2
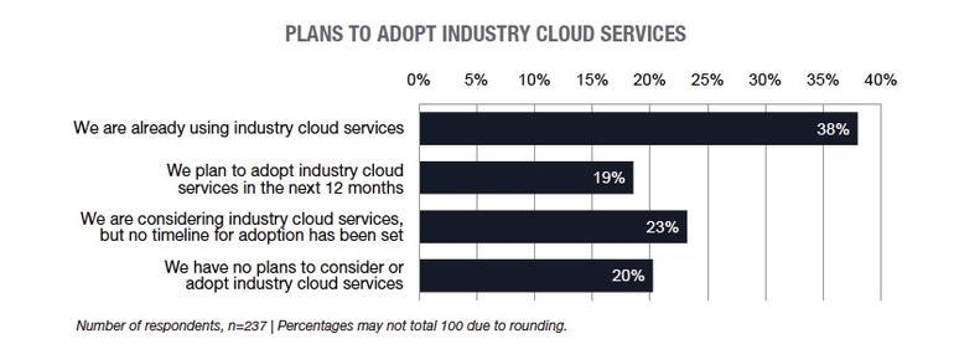
Image: Tech Pro Research
However, not all clouds are the same and not one type of cloud computing is right for everyone. Several different models, types, and services have evolved to help offer the right solution for your needs. First, you need to determine the type of cloud deployment, or cloud computing architecture, that your cloud services will be implemented on. 1
Cloud computing spans a range of classifications, types and architecture models. The transformative networked computing model can be categorized into four major types: Public Cloud, Private Cloud, Hybrid Cloud and Multi Cloud. 3
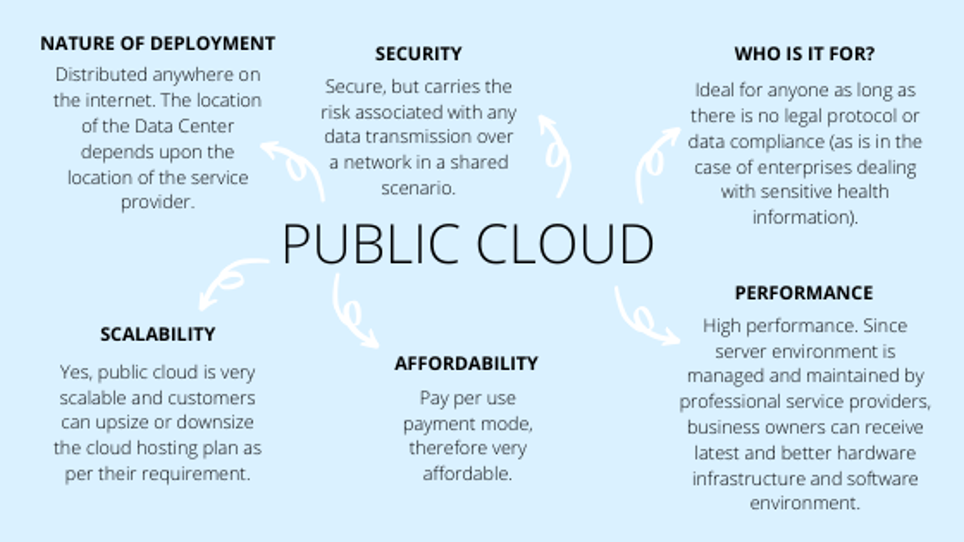
1. Public Cloud and Private Cloud
The Public Cloud, a pay per use model, is a cloud infrastructure with all the services available through the web, so the computing infrastructure can be shared among multiple organisations. This model is owned and operated by service providers.
On the other hand, the Private Cloud is a business-specific infrastructure exclusively designed for individual companies. It provides options for hosting the data either on-site or at the service provider’s data centre.
Advantages for businesses 4 :
|
Public Cloud |
Private Cloud |
|
Scalability – Virtual machines within the system can be created, scaled and shut-down in an instant. |
Enhanced security and privacy – Can be isolated from all but the company who owns it. |
|
Cost – Service can be implemented at a fraction of the cost it would take to implement a Private Cloud alternative. |
Total control – You are free to build and configure your Private Cloud in any way you like. |
|
Management – You will be free from the responsibility of maintaining and managing the infrastructure. |
Increased performance – The resources within your private cloud infrastructure are at the disposal of your company and your company alone. |
|
|
Improved reliability – Private Cloud offers a greater degree of reliability thanks to a fault resilient and redundant architecture that isn’t shared in any way. |
|
|
Increased flexibility – Virtual machine can be scaled up and down seamlessly. |
Disadvantages for businesses [5][6] :
|
Public Cloud |
Private Cloud |
|
Security – You can only customise security factors at the operating system level – security at the physical level is under the purview of your supplier and they are also by default, visible internet-wide leading to the increased levels of remote scanning for vulnerabilities. |
Cost – With exclusivity comes increased cost. |
|
Inflexibility – Although virtual machines are very flexible in terms of scale and power, some choices may be made for you by the hosting provider. |
Under-utilisation – With a private cloud, the cost of capacity under-utilisation is a cost to you, not to your provider. Therefore managing and maximising utilisation becomes your concern. |
|
Compliance – Have to consider the legal requirements around data management. |
Platform scaling – Large upward changes in your requirements are likely to require scaling of the physical infrastructure. |
What kind of organisation will benefit from the Public Cloud model?
The Public Cloud model is ideal for anyone as long as there is no legal protocol or data compliance (enterprises dealing with sensitive health information). Highly suited for organisations that aren’t infrastructure-, security-specific. Also companies that would like to store non-sensitive data can utilize this model to its fullest for their operations.
What kind of organisation will benefit from the Private Cloud model?
The Private Cloud model is recommended for government agencies, hospitals or businesses handling classified data, exclusively for organisations planning to store sensitive or private data. Though expensive, this model is highly efficient, secure, and safe. 4
2. Hybrid Cloud and Multi Cloud
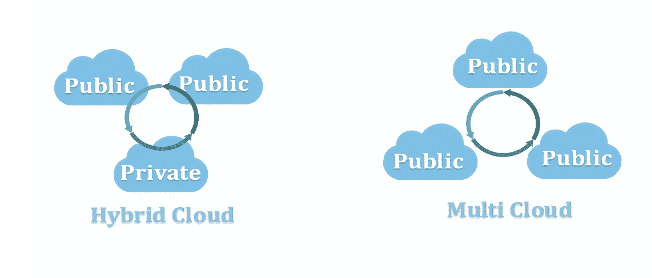
The Hybrid Cloud model is a combination of Public and Private systems. Small and medium businesses that want to leverage both cost-effectiveness and robust data security, control and privacy will invest in this type of model. 4
“Multi-cloud” describes a strategy on the other hand, while “hybrid cloud” is a new type of infrastructure.
The confusion between hybrid cloud and multi-cloud is compounded by the fact that they’re often used interchangeably. While the two terms are related, they describe two distinct (but both important) concepts. Understanding the difference can help ensure the success of your overall cloud strategy. 8
Differences between Hybrid Cloud and Multi Cloud:
|
Hybrid Cloud |
Multi Cloud |
|
The pairing of a private cloud with public cloud |
The pairing of multiple public clouds but can also incorporate physical and virtual infrastructure (including private clouds) |
|
Hybrid Cloud cannot have the multi-cloud approach |
Multi cloud may include hybrid cloud |
|
Relies on a private data centre |
Organisations may choose one service provider for IaaS and another for SaaS |
Advantages of Hybrid Cloud and Multi Cloud for businesses: 4
|
Hybrid Cloud |
Multi Cloud |
|
Security – Including private cloud in the mix gives reassurance when it comes to security of your most sensitive operations. |
Lower risk of DDoS attacks – Makes your company’s services resilient against these types attack because even if one cloud goes down, others remain available to take the load until your service recovers.
|
|
Cost efficiency – Hybrid cloud adopters can balance their need to be cost efficient with the security of keeping their most sensitive and critical workloads on private cloud. |
Power of Choice – Able to play the field and explore different providers to find the best match for each part of your business to line up its functionality for a perfect fit. |
|
Scalability – Critical data, assets, and operations can continue to reside in the private cloud, but organizations can now leverage the expansive power of cloud computing to quickly and efficiently increase their operational capacity. |
Reliability – Using multiple clouds to host your various components is the ultimate form of redundancy, making for fewer SPOFs.
|
|
Flexibility – The “pick and mix” style of hybrid cloud gives organisations the chance to explore a variety of operational directions and find the optimum cloud solution for them. |
Flexibility – By employing more than one cloud-hosting company, particularly a mix of private and public ones, you can match your needs to the solutions that fit the best, and alter them as the need fits. |
|
Preservation of investments – Enables you to continue using existing IT investments, whether on premises or co-located. |
Avoiding vendor lock-in – Avoid putting yourself in the position of having to accept any sort of restructuring of agreements or price schedules from that company because you’re locked into doing business with them. |
|
|
Cost-performance optimization – Finding the right combination of cloud providers to match your business needs and your checkbook can give your company an extra boost of efficiency while dropping your costs accordingly. |
|
|
Data management – Rather than lump all your data into one cloud, you can diversify to take advantage of the right service for the right function. |
|
|
Power of managed clouds – While the managed clouds take care of specific units, others can serve you best for security or processing purposes. |
Disadvantages of Hybrid Cloud and Multi Cloud for businesses: [9][10]
|
Hybrid Cloud |
Multi Cloud |
|
Added complexity – It is more complex to manage a Wide Area Network as opposed to a single site’s network or simply utilizing a public cloud’s network. |
Management Complexity – Using services from several cloud vendors increases the complexity of management. |
|
Data transfer bottlenecks – Networking bottlenecks are highly dependent upon the underlying infrastructure and the nature of the packets being sent across the network and with big data, this can easily become a performance bottleneck. |
Complex Structures – The complex structure of heterogeneous environments leads to difficulties in developing cross-platform applications. |
|
|
Security concerns – Additional security concerns and adds new attack vectors for applications. |
|
|
Monitoring complexity – If you use cloud services that include containers, that adds an additional layer of complexity for monitoring. |
|
|
Cost overhead – Adds complexity in controlling cloud spending. |
|
|
Migration challenges – This process will require time and specific skills that aren’t always available in-house. |
What kind of organisation will benefit from the Hybrid Cloud model?
The Hybrid Cloud model is a good choice for e-commerce setups as well as small or big sized corporations handling sensitive data on behalf of their clients. While Public Cloud offers more scalability, Private Cloud ensures security and Hybrid provides the benefits of both. 4
What kind of organisation will benefit from the Multi Cloud model?
Use of multi-clouds are critical for organisations who want to avoid cloud service provider (CSP) lock-in. A multi-cloud strategy enables companies to use best of breed cloud services from the plethora of service providers in the market. 11
Summary of Public vs Private vs Hybrid vs Multi Clouds
Wrapping Up
The choice between public, private and hybrid cloud solutions depends on a variety of factors, use cases and limitations. All cloud models have their own set of limitations and benefits. It completely depends on the requirements of the businesses to pick the right model that fits their purpose and needs. It is not an either/or situation, especially since organisations tend to leverage all four types of cloud solutions considering the inherent value propositions and tradeoffs.
While these concerns and drawbacks are important to address, if catered in controlled environments, utilizing appropriate experts, and resources, the right cloud model can be a total win for your organisation.
Having a hard time finding the right cloud model for your business? We can help!
If you wish to find out more information on Cloud Computing, you can visit us at Netpluz 24/7. Alternatively, you may book an appointment by submitting your information here for a free consultation.
References:
- “What Is Cloud Computing? A Beginner’s Guide: Microsoft Azure.” What Is Cloud Computing? A Beginner’s Guide | Microsoft Azure, azure.microsoft.com/en-us/overview/what-is-cloud-computing/
- Maddox, Teena. “Research: 80 Percent Using or Considering Industry Cloud Services.” ZDNet, ZDNet, 1 Apr. 2015, www.zdnet.com/article/research-80-percent-using-or-considering-industry-cloud-services/.
- Raza, Muhammad. “Public Cloud vs Private Cloud vs Hybrid Cloud: What’s The Difference?” BMC Blogs, 12 Sept. 2018, www.bmc.com/blogs/public-private-hybrid-cloud/.
- “Public vs. Private vs. Hybrid -Tips to Choose the Best Cloud Model for Your Business.” Impiger, www.impigertech.com/resources/blogs/public-vs-private-vs-hybrid-cloud.
- Dufficy, Tim Pat. “What Is Public Cloud? – Plus the Advantages and Disadvantages for ISVs.” What Is Public Cloud? – Plus the Advantages and Disadvantages for ISVs, www.serverspace.co.uk/blog/blog/public-cloud-plus-advantages-disadvantages-isvs.
- Dufficy, Tim Pat. “What Is Private Cloud? Advantages and Disadvantages.” What Is Private Cloud? Advantages and Disadvantages, www.serverspace.co.uk/blog/what-is-private-cloud-plus-advantages-disadvantages.
- Gupta, Kitty. “Hybrid Cloud vs Multi-Cloud: What You Need to Know.” FreelancingGig, 9 Nov. 2019, www.freelancinggig.com/blog/2019/11/09/hybrid-cloud-vs-multi-cloud-what-you-need-to-know/.
- O’Reilly, Dennis, and Dennis O’Reilly. “Multi-Cloud and Hybrid Cloud: A World of Difference – DZone Cloud.” Dzone.com, 1 June 2018, dzone.com/articles/multi-cloud-and-hybrid-cloud-a-world-of-difference.
- “The Hybrid Cloud: Pros and Cons of Hybrid Cloud Computing.” Exit Technologies, 5 Sept. 2019, www.exittechnologies.com/blog/cloud-computing/advantages-disadvantages-hybrid-cloud/.
- User, Super. “Multi-Cloud Computing: Pros and Cons for Enterprise.” Apriorit, ApriorIT, 9 Aug. 2018, www.apriorit.com/dev-blog/552-multi-cloud-computing.
- “Why Multi-Cloud Has Become a Must-Have for Enterprises: Six Experts Weigh In.” Ubuntu, ubuntu.com/blog/why-multi-cloud-has-become-a-must-have-for-enterprises-six-experts-weigh-in.
#cloud #computing #businesses #enterprises #public #private #hybrid #multi #advantages #disadvantages #model
Author: Toh Wei Ting https://sg.linkedin.com/in/tohweiting
With the current outbreak of Coronavirus (2019-nCoV), officially named “Novel Coronavirus Pneumonia” or NCP by Chinese Health Authorities in China, businesses in the region have started to relook at their Business Continuity Plan (BCP) on how to effectively maintain business operation where physical contact between employees or individuals is being restricted to a high degree. Enterprise Singapore, supported by Singapore Business Federation has published a comprehensive Guide on Business Continuity Planning for 2019 Novel Coronavirus.
The gathering of a large group of employees in offices is now being avoided as much as possible, with companies instructing certain percentage of its employees to work away from the office or from home as much as possible to reduce the chance of infection risks in the office space.
In short, the standard business operations using the traditional mindset of mandating all staff to report to the office might now be a risky decision, in terms of risk of infection. However, this is highly dependent on the nature of business – such as operators for heavy machinery are still required to report to work, or telemarketers only requiring a laptop and internet to work. The reliance on digital communication channel is now critical as this is something that the current coronavirus cannot take advantage of. And NO, I’m talking about the actual infection and not cybercriminals taking this opportunity for email phishing or creating malware in the name this outbreak.
If you are one of many businesses that have not put in place a robust Business Continuity Plan (BCP) to mitigate current risks, now is the time to relook at your business operations, processes and infrastructure and do something about it. The authorities have mentioned that it could take months before this outbreak is over. They have also mentioned that the coronavirus is more infectious than Severe Acute Respiratory Syndrome (SARS) that was discovered and recognised in February 2003, however, Coronavirus fatality rate is lesser, according to the authorities.
Businesses should put the focus on considerations on the short-term situation where employees may be restricted to work outside of the office as much as possible. Businesses will need to rely on the current digital infrastructure, or even look into new solutions to support the sudden surge of digital communication requirements.
For companies with robust BCP in place, working remotely from home may not be a problem. In Netpluz, we allow our employees to apply for telecommuting, or work from home in case a need arises. Netpluz utilises the Microsoft O365 platform where our employees are able to conduct their day to day operations, such as conferencing, file-sharing or even work together on a single document. The platform enables our employees to maintain constant contact with each other via this platform. CRM & ERP platforms are accessible through Virtual Private Network (VPN). Sensitive data are being encrypted before being transmitted between employees’ laptop remotely and servers in Netpluz private cloud.
Video conferencing between employees, particularly the usual weekly meetings on business operations updates, shown no issues as Netpluz infrastructure is robust and highly available. Kudos to the engineering team and their experiences.
For customer-facing staff, such as the sales team, the inability to meet will not be the main factor that affects operations. The sales team may consider inviting their customers/prospects to meet through video conferencing with Microsoft Teams on Microsoft O365 platform.
For companies who are not well-prepared, such as not utilizing Microsoft O365 or similar platform and only relying on the traditional communication channel such as Whatsapp and traditional telephone, the predictable outcome would be employees not being able to work productively.
The following are some recommendations for businesses wanting to ensure business continuity:
- Consider categorising your employees in at least 2 teams (Team A & Team B), and avoiding physical interactions between the 2 teams.
Recommendation: Have at least a team to work remotely from home. Ensure that either team will be able to take on the role of the other team, should the need arises.
- Enabling your IT department/staff to deal with the sudden surge of connectivity issue, as more and more employees may be required to work from home.
Recommendation: Understand your bandwidth usage/utilization and upgrade to a higher bandwidth if necessary.
- File servers are hosted on-premise in the office location.
Recommendation: With the mobile workforce, a simple Virtual Private Network (VPN) connectivity is the basic requirement to access the file servers in the private network. Do contact us if you need VPN setup or even consultancy on your current infrastructure to support this feature.
- Ensure your employees are able to work from anywhere such as from home. Many SMEs, especially smaller companies have yet to collaborate digitally, as most may still prefer the in-person face to face meeting.
Recommendation: Consider working on Microsoft O365 and collaborate online with Microsoft Teams. Teams can be installed on multiple devices and employees can also work on their mobile phones on the go.
Netpluz is a Microsoft SPLA partner and Cloud Solution Provider.
- Ensure that all employees who work remotely do have the communication channel such as mobile phone to be contacted or to contact their customers or suppliers.
Recommendation: Ensure that employees desk phones are properly set up to ensure call forwarding. A solution such as MobileRoam ensures that employees are able to communicate with parties more productively. This service is recommended for employees that might be facing limited mobile plan subscribed. Businesses may also consider Cloud PBX and IP-Phones should the nature of the business requires high volume call traffics.
- Ensure that all employees’ endpoint such as laptops is installed with endpoint protection.
Recommendation: With employees working remotely and accessing the internet publicly, there will always be cyber risks of malware. To ensure that endpoints are properly secured with antivirus and anti-malware, Netpluz recommends Sophos Endpoint Protection such as Intercept X Advanced with EDR and MTR.
- All endpoints should have a proper backup solution in place.
Recommendation: As employees will move around to work remotely, there will always be a chance that the endpoint they work with will be stolen, lost or even data corruption. Having a proper endpoint backup solution such as Druva InSync ensures proper data protection and governance in this critical period.
- Working from home is not an option due to the nature of business, e.g. Financial or Sensitive Data Handling.
Recommendation: In such a scenario, businesses may consider splitting their team B onto a secondary work area, similar to business Work Area Recovery (WAR), which is also covered under a comprehensive BCP plan. Such secondary workspace or Work Area Recovery solutions include complete office facilities and equipment such as PCs, telephone systems, facsimile, photocopier, manager rooms, meeting rooms and general office areas to which our customers can quickly relocate key personnel to the recovery site and resume business as soon as possible. Contact Netpluz today to find out more, from cost-effective solution to a full-fledged WAR room.
- Businesses to relook at existing or even consider building a Business Continuity Plan (BCP).
Recommendation: As IT landscapes are getting more complex with the subscription of multiple SaaS solutions or even on-prem solutions, devising a comprehensive and robust business continuity plan may require the guidance or advisory from a managed communication service provider who has decades of experiences. Netpluz has been offering advisories in terms of BCP on IT infrastructure.
The above recommendations are some simple guidelines to enable your employees to continue to work remotely if required while waiting for the coronavirus outbreak to subside.
Solutions such as collaboration platform Microsoft Teams on O365 creates the modern workspace, where employees can collaborate without the need to be physically in a specific office. Companies that have proper BCP in place would have a competitive advantage in this crisis period.
For businesses who finally understands the importance of digital communication platforms and in need of assistance, Netpluz can advise, propose, implement and manage an end-to-end robust solution. Please contact contact@netpluz.asia to set up an appointment to discuss how Netpluz can support you in communication services.
Author: Rueburn Liang
Cyber Security is the protection of not only internet-connected systems (including hardware, software or electronic data) from theft or damage by cybercriminals but also from disruption of services following a successful cyber-attack.[1] According to the Cyber Security Agency of Singapore, 378 business email impersonation scams were recorded in 2018. This led to businesses in Singapore suffering close to S$58 million in losses. [2] Cybersecurity Ventures has reported that businesses will lose approximately $6 trillion to cyber-crime by 2021. [3]
One of the key challenges faced by organisations today is implementing cybersecurity measures to protect their internet-connected systems from the continuously evolving nature of cyber-attacks. And according to Code 42, 78% of security professionals believe that the biggest threat to cybersecurity is the negligence of employees. [4]
Cybercriminals exploit the weakest links in an organization’s IT security fabric. Often, the weakest link in any organisation is the employees. And yet a study of over 5,000 businesses around the globe by Kaspersky Lab and B2B International found that just over half of businesses (52%) believed that their cybersecurity would be at risk because of their employees. [5]

Common Cybersecurity Mistakes Made By Employees
In this section, we’ll be looking at the four principal errors made by employees that could expose organisations to cyber-attacks
1. Weak and Vulnerable Passwords
According to security experts, poor password management contributes to 81% of the data breaches.[6] With employees utilising the same password for multiple accounts, not changing passwords on a regular basis and using weak passwords (some examples as shown in the table below) put organisations at risk. [7]
Examples of weak passwords:
|
Password |
Type |
|
kathy5 |
Name-based |
|
Qwerty |
Keyboard sequence |
|
AbcAbc |
Repeating sequence |
|
dr1v3way |
Word-based with common letter and number substitution |
- Weak or Outdated Security Software
Keeping security software, web browsers and operating systems updated with the latest protection will deter cybercriminals from leveraging system vulnerabilities. However, many organizations do not keep up with the updates or fail to understand the consequences of not doing so. The consequences of an employee’s negligence could lead to a ransomware outbreak where the virus encrypts and locks all the files on the computer. The attacker then demands a ransom from the victim to restore the access of the data upon payment. [7]
Here is a diagram to illustrate how a Ransomware Attack is executed:
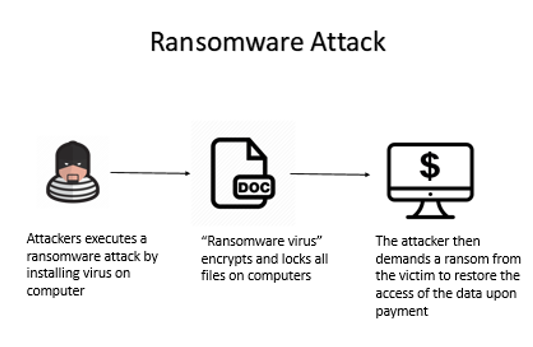
- Lax Email Practices
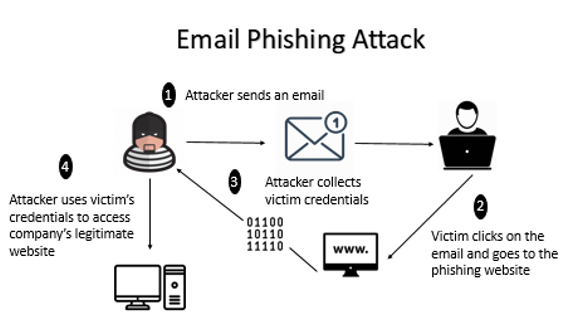
Despite repeated warnings against responding to unsolicited emails or text messages, employees continue to be targets of cyber-attacks such as phishing, social engineering, and smishing. These attacks occur when an attacker sends an email link to the victim. Upon clicking on the link, the victim will be directed to the phishing website where the attacker is able to collect the credentials of the victim. The attacker then uses the victim’s credentials to access the legitimate company’s website. [7]
Here is a diagram to illustrate how Email Phishing Attack is executed:
- Using Unsecured Networks
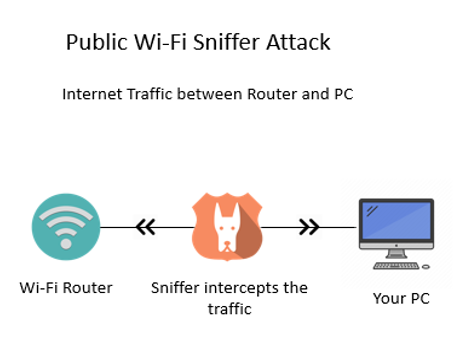
Utilising company devices on unknown networks increases the risk of cyber-attacks since data may not be encrypted over these networks and could easily be intercepted and subsequently stolen. For example, login details information can be revealed when there is an attempt to access emails on a public network. [7]
Here is a diagram to illustrate how a Public Wi-Fi Sniffer Attack is executed:
How can your company reduce these vulnerabilities?
In recent years, cyber-attacks have become more sophisticated and persistent due to weak security regulations enforced by companies. By now, you might be wondering how you could protect your data better. Sophos Intercept X Advanced with EDR and Druva inSync offer some possibilities that could help companies overcome poor practices done by their employees. These two products address the business challenges faced by organisations such as data protection, secure file sync and sharing, etc.
What is Sophos Intercept X Advanced with EDR?
Sophos Intercept X Advanced with Endpoint Detection and Response (EDR) is designed to stop the widest range of attacks. It can detect malware, provide exploit protection, defend against ransomware and more through a combination of modern and leading-edge foundation techniques. In an event of malicious activity, EDR provides users with a complete solution by providing them with a detailed report of the attack. This helps businesses understand the root cause of the attack and help them to avoid future cyber-attacks. [8]
Benefits of Implementing Sophos Intercept X Advanced with EDR

1) Deep Learning Malware Detection
Intercept X’s artificial intelligence is a deep learning neural network, an advanced form of machine learning that detects known and unknown malware without relying on signatures. Powered by deep learning detection, Intercept X has the best malware detection platform in the industry. This allows Intercept X to detect malware that slips by other endpoint security tools. [8]

2) Secured Data & Files
Intercept X utilises CryptoGuard technology to combat cyber security attack such as ransomware and boot-record attacks, making it the most sophisticated anti-ransomware technology available. Even if trustworthy files or processes are manipulated or stolen, CryptoGuard is able to interrupt and revert them to their original state. [8]
3) Detailed Report Analysis
With EDR, most threats are stopped before they can cause damage. Intercept X Advanced with EDR provides additional cybersecurity assurance with the ability to detect, investigate and respond to potential security threats. Thus, when a potentially suspicious file is detected the administrators are provided with an analysis of what the malware did and how it was executed. This helps your companies to understand the threats better and prevent them. [8]
Here is a quick overview of how Sophos Intercept X Advanced with EDR works:
What is Druva inSync?
Druva inSync provides a comprehensive solution for enterprise-grade data protection and management. It allows users to view their data sources and usage activities to ensure compliance. Administrators are also updated of any potential data risks that have been detected. Data collected are stored in a central repository, giving end-users seamless and constant access to the information. [9]
Benefits of Implementing Druva inSync
1) Centralised Data
Druva inSync allows collection of data through multiple devices like mobile phones and cloud-based applications. The collected data will be then stored and indexed in a central repository which makes it easier for an IT department to implement company policies. [9]

2) Real-Time Data Monitoring
Druva inSync is equipped with an administrative dashboard where users can monitor their data activities and data usage in real-time. This allows administrators to easily discover compliance issues and resolve them quickly before they grow into larger problems. Real-time data monitoring also keeps your organisations safe. [9]
3) Ease of Compliance Enforcement
Druva inSync helps you save time when it comes to administering policies and regulations. This system comes with pre-configured compliance templates like PCI, GLBA and HIPPA. It also enables users to customise and create their own templates. Whichever template one chooses, one can be ensured that the app automatically search for any data risks. [9]

What other solutions can you integrate along with Sophos?
Cyber-attacks are carried out mostly through emails and unsecured networks. This could be resolved by integrating the following products with Sophos Intercept X Advanced with EDR. [10]
|
Solutions: |
Features: |
|
Intercept X and Sophos Email |
✔ Validates if malware has been installed on devices with compromised mailboxes |
|
Intercept X and Sophos Wireless |
✔ Blocks worm-like lateral movement, automatically isolating infected machines ✔ Prevents non-compliant devices from connecting to corporate data |
Summary- Sophos Intercept X Advanced with EDR and Durva Insync
There are many comprehensive cyber security products available in the market to mitigate cyber-attacks. Needless to say, the product chosen to safeguard the data plays a major role in preventing cyber-attacks against your companies.
Here is a quick summary of the benefits of Sophos Intercept X Advanced with EDR and Durva InSync:
|
|
Sophos Intercept X Advanced with EDR |
Durva inSync
|
|
Deep Learning Malware Detection |
✔ |
|
|
Secured Data Files |
✔ |
|
|
Detailed Report Analysis |
✔ |
✔ |
|
Centralised Data |
|
✔ |
|
Ease of Compliance Enforcement |
|
✔ |
|
Software Supported |
Windows 7 and above, 32 and 64 bits |
● Microsoft Office ● G Suite ● Box ● Salesforce |
The following are the factors that are needed to be taken into consideration when choosing between these 2 products. The key difference between these two products is that Sophos Intercept X Advanced with EDR protects internal data stored in the physical hardware whereas Druva inSync supports data stored on the cloud premises.
If you wish to find out more information on Sophos Intercept X Advanced with EDR or Durva inSync, you can visit us at Netpluz. Alternatively, you may book an appointment here for a free consultation.
Author: Jeyani D/O Ravichandran
References:
- “What Is Cybersecurity?” Cisco, Cisco, 10 Dec. 2019, https://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html.
- Tay, Rachel. “Businesses in Singapore Lost Nearly S$58 Million to Email Impersonation Scams Last Year: CSA Report.” Business Insider Singapore, 19 June 2019, https://www.businessinsider.sg/businesses-in-singapore-lost-nearly-s58-million-to-cyber-attacks-last-year-csa-report/.
- Cybercrimemag. “Cybercrime Damages $6 Trillion by 2021.” Cybercrime Magazine, 9 Dec. 2018, https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/.
- Kratikal Tech Pvt Ltd. “Humans Are the Weakest Link in the Information Security Chain.” Medium, Medium, 6 Mar. 2018, https://medium.com/@kratikal/humans-are-the-weakest-links-in-cyber-security-of-any-organisation-ac04c6e6e71.
- “The Human Factor in IT Security: How Employees Are Making Businesses Vulnerable from Within: Kaspersky Official Blog.” Daily English Global Blogkasperskycom, https://www.kaspersky.com/blog/the-human-factor-in-it-security/.
- “81% Of Company Data Breaches Due to Poor Passwords.” TraceSecurity, 10 Dec. 2019, https://www.tracesecurity.com/blog/articles/81-of-company-data-breaches-due-to-poor-passwords.
- Mical, Jason, et al. “11 Ways Employees Can Be Your Weak Link for Cybersecurity.” Security Boulevard, 9 Sept. 2019, https://securityboulevard.com/2019/09/11-ways-employees-can-be-your-weak-link-for-cybersecurity/.
- SOPHOS Intercept X, SOPHOS, https://www.sophos.com/en-us/medialibrary/PDFs/factsheets/sophos-intercept-x-dsna.pdf.
- “Druva InSync Review: Pricing, Pros, Cons & Features.” com, 12 Aug. 2019, http://comparecamp.com/druva-insync-review-pricing-pros-cons-features/.
- “Synchronized Security.” Synchronized Firewall & Endpoint Protection with Sophos, https://www.sophos.com/en-us/lp/synchronized-security.aspx.
Importance of cybersecurity for cyber-attacks
Why do we have fire drills when we hardly or never encounter fire? The same goes for cybersecurity – we do not know when we will encounter a cyber-attack. Cybersecurity is the practice of protecting systems, networks and programs from digital attacks. Successful cybersecurity has multiple layers of protection spread across computers, networks, programs or data that one intends to keep safe. 1
Impact of cyber-attacks on companies
Cyber-attacks can cause financial loss for the business as well as reputational damage. When there is a loss in customers’ data to hackers, it has resulted in a fall of many companies. Companies have risk falling into endless lawless and may declare bankruptcy when customers’ data are stolen by hackers. Data recovery takes time and can be very expensive. 2 Due to reputational damage to the company, customers will lose trust in it and hence venture to other companies. Therefore resulting in a loss of profits and sales.
In March 2018, data tied to Under Armour’s fitness application was breached and affected 150 million users. Information such as user names, email addresses, passwords was stolen but users’ credit card data and social security or driver’s license numbers were not breached. During after-hours trading, Under Armour’s stock dropped more than 2%. 3
Ways employees’ actions make companies vulnerable to cyber attacks
- Outdated software
The software requires ongoing updates and upgrades. Software becomes outdated when it does not have updates to support it.4 According to PC Trends report 2019,5 1 in 6 Windows 7 users and 1 in 10 Windows 10 users are using an outdated operating system version. Outdated software does not have patches if vulnerabilities are found, resulting in more advanced cyber-attacks. Therefore, it is important to update the software as not updating it expose the business to vulnerabilities and security risks.

- Weak login credentials
Employees having weak or the same passwords across multiple accounts can allow cyber-attacks to take place easily. Principle researcher, Jarno Niemela at F-secure 5 stated that the Brute force attack is the primary way hackers use to bypass the security. It is accounted that 31% of cyber-attacks used this method to hack into their target. Brute force attack means inputting as many passwords possible, seeing if it works against their target. Hackers even have automated scripts that can find a way around simple protection, such as the maximum number of tries of passwords within a certain time window. 6 Hence a simple and common password can easily fall prey to the next cyber-attack.

- Opening unknown emails
In today’s world, emails are the most preferred way of communications when it comes to business-related context. Companies normally collect and stores a huge amount of personal data.7 In order for all of these personal data to be well taken care of, employee’s knowledge and care can play an enormous part in preventing a cyber-attack from happening. A research done by ‘The Radicati Group’8 shows that an average person needs to go through 235 emails a day. With these large amounts of emails, it is not surprising that some may contain scams in the form of attachments or links. With an accidental click, employees may be opening the gates to those cybercriminals into the company’s digital home.
Products available to reduce cyber attacks

Endpoint protection with EDR
EDR means endpoint detection and responses. Its solutions are designed to monitor and respond to advanced internet threats continuously.
- Remove malware
Endpoint protection provides simple security for business. It automatically removes malware when detected or isolates comprised devices in order to prevent damage. Below are some ways of how endpoint protection removes malware. 9
-
- Isolate devices
In order to prevent the problem from spreading further, part of rectifying a problem is to put it in quarantine. Comprised devices will be isolated when necessary until companies ensure they are safe.
-
- Threat removal
As employees may not be aware of malicious links, attachments or downloads, cyber-attacks may occur once employees click onto those. Therefore with endpoint protection, it will help to remove if anything malicious is found. It is simple and automatic.
-
- Synchronised security
Synchronised security transforms threat detection when threat discovery, investigation and response are automated. The incident response time is reduced exponentially and tactical resources can be refocused on strategic analysis.
- Decloaking malware
-
- Behavioural analytics
It helps to find out any suspicious behaviours and allow the detection of malware that is specifically designed to avoid traditional solutions.
-
- Traffic detection
It helps to pre-filter all Hypertext Transfer Protocol (HTTP) traffic and tracks suspicious traffic. Additionally, the file path of the process for the sending of malicious traffic.
-
- Integrated endpoint and network
Suspected system of what exactly firewall is detecting is alerted when there is immediate and automatic communication between Endpoint and Network. It allows the endpoint protection agent to instantly use the information to find out the process behind the attack.
Endpoint backup
Endpoint backup ensures regulatory compliance and improves data visibility for a mobile workforce. It allows employees to protect the corporate data at their convenience. It helps to protect and manage the data across all endpoints such as laptops and smartphones. The unified visibility and search across the data deliver fast identification for governance. To ensure zero-impact to the productivity of end-users, lightweight with tunable resource controls are used. 10
Summary
|
Technology |
Benefits |
|
Endpoint protection with EDR |
· Removes malware o Isolate o Threat removal o Synchronised security
· Decloaking malware o Behavioural analytics o Traffic detection o Integrated endpoint and network |
|
Endpoint backup |
· Ensures regulatory compliance · Improves data visibility · Protects cooperate data at convenience · Fast identification · Zero impact to productivity |
Conclusion
Your company can be a victim of cyber-attack just because of a small mistake made by your employees. Prevent your company from having reputational damage and facing financial losses due to cyber-attacks. Act fast before it is too late!
Click here to find out more about ways or products available to protect your data, or email us to arrange for an appointment with our experienced manager. We will provide ways for you to become more secure.
Author: Toh E Pyn
References
- Services, P. (2019). What Is Cybersecurity?. [online] Cisco. Available at: https://www.cisco.com/c/en_sg/products/security/what-is-cybersecurity.html [Accessed 11 Dec. 2019].
- com. (2019). How cyber attacks impacts business.. [online] Available at: http://www.webrtcworld.com/topics/from-the-experts/articles/440430-how-cyber-attacks-impacts-business.htm [Accessed 11 Dec. 2019].
- Anon, (2018). Under Armour announces data breach, affecting 150 million MyFitnessPal app accounts. [online] Available at: https://www.washingtonpost.com/news/the-switch/wp/2018/03/29/under-armour-announces-data-breach-affecting-150-million-myfitnesspal-app-accounts/ [Accessed 11 Dec. 2019].
- Parker Software. (2019). The security risks of outdated software – Parker Software. [online] Available at: https://www.parkersoftware.com/blog/the-security-risks-of-outdated-software/ [Accessed 11 Dec. 2019].
- Windows Report | Error-free Tech Life. (2019). 55% of Windows PCs are running outdated software [Security Alert]. [online] Available at: https://windowsreport.com/outdated-software-security-risks/ [Accessed 11 Dec. 2019].
- Palmer, D. (2019). Ransomware attacks: Weak passwords are now your biggest risk | ZDNet. [online] ZDNet. Available at: https://www.zdnet.com/article/ransomware-attacks-weak-passwords-are-now-your-biggest-risk/ [Accessed 11 Dec. 2019].
- com. (2019). Weak and Stolen Passwords | WatchGuard Technologies. [online] Available at: https://www.watchguard.com/wgrd-solutions/security-topics/weak-and-stolen-passwords [Accessed 11 Dec. 2019].
- com. (2019). [online] Available at: https://www.kaspersky.com/resource-center/preemptive-safety/7-ways-to-cyberattack-vulnerability [Accessed 11 Dec. 2019].
- com. (2019). [online] Available at: http://www.radicati.com/wp/wp-content/uploads/2015/02/Email-Statistics-Report-2015-2019-Executive-Summary.pdf [Accessed 11 Dec. 2019].
- com. (2019). Sophos Endpoint Protection. Advanced Security with Intercept X.. [online] Available at: https://www.sophos.com/en-us/products/endpoint-antivirus.aspx?cmp=36476&utm_source=GoogleSearch&utm_medium=cpc&utm_campaign=MG-ASEAN-GoogleSearch&utm_content=SM100289&gclid=Cj0KCQiA_rfvBRCPARIsANlV66MbtXXPIGuBJKxEogN28oUqQ4DVaWc9RDWV4eCoEqvCVa3-wTPZn7IaAkVnEALw_wcB [Accessed 11 Dec. 2019].
An ounce of prevention through Vulnerability Assessment and Penetration Testing (VAPT) is worth a pound of cure
We all have witnessed the notorious cyber-attacks like WannaCry and NotPetya/ExPetr.1 These high profile attacks have resulted in large disruptions, forcing businesses to halt their operations that may cost them billions of dollars.
According to Accenture, 43% of cyberattacks are targeted towards small businesses. Yet, only 14% are capable of defending against these malicious attacks.2
Obviously, a comprehensive security service will incur additional expenses. However, according to Hiscox, these cyber-attacks can cost your business on average $200,000 regardless of the scale of your business.2
Regardless of the size and scope, your business is greatly vulnerable to cyber-attacks. It is not a matter of if, but it is a matter of when you will be the next target of the hackers’ “hit list”. When it happens, your business may suffer unfathomable consequences.
Stay Free from Cyber Attacks
Now knowing your vulnerability, how can you prevent such malicious cyber activities from occurring? The most ideal and unsurpassable method is through Vulnerability Assessment and Penetration Testing (VAPT). So, you might wonder what this long piece of jargon is about and how and how it is going to protect your business.
This blog article will provide you with some valuable information on:
1. A better comprehension on VAPT
2. How VAPT is executed
3. How VAPT will improve your IT security
What is Vulnerability Assessment & Penetration Testing (VAPT)? 3
To put it in the simplest terms, Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive and extensive testing process. Its goal is to identify security flaws in your network, application or program.
As the name implies, there are two separate components to perform VAPT. Both Penetration Testing and Vulnerability Assessment execute two completely different types of security tests:
- Vulnerability Assessment: Finds flaws and vulnerability in software, network or program. In other words, to assess how defenceless your systems are.
- Penetration Testing: Conducted after identifying the Vulnerabilities. Security professionals will check and exploit the existing vulnerabilities identified in the software, network or program.
What is Vulnerability Assessment?
By pure definition, the word “Vulnerability” means being exposed to the possibility of getting attacked or harmed. Similarly, a Vulnerability Assessment will provide you with a list of possible security vulnerabilities in your company’s network.
Vulnerabilities can be the result of weak passwords, software errors, wrong software settings, computer virus, or other forms of malicious script or SQL injections.4
Vulnerability Assessment is performed using a non-intrusive approach. With the amalgamation of manual and automated scans, this will enable you to identify security flaws that may be exploited during a cyber-attack.
Here is an example to give you a better grasp on what is a vulnerability and an exploit: If an intruder could bypass the security guard at the front gate by entering the building through a backdoor – this is a vulnerability. If he/she actually get into the building – this is an exploit. It is important to understand the difference between these two words as we will be using it frequently in this blog.
What is Penetration Testing? 3
On the contrary, Penetration Testing employs an intrusive approach. Why would we say it is intrusive? Well, penetration testers would actually attempt to exploit identified vulnerabilities to gain unauthorized access into your IT infrastructure. In a way, it emulates a “real attack” to your IT network.
Upon successfully performing a penetration test, this would allow you to determine how robust your organisation is when it comes to defending your IT network.
The following information will help you understand how these tests are performed for your business.
How are Vulnerability Assessments Performed? 5
As mentioned previously, manual and automated testing tools are utilised to scan your IT infrastructure and environment for known vulnerabilities. During the assessment process, it involves three periodic steps: Assessment, Identifying Exposures and Addressing Exposures. Let’s look at each phase briefly:
1. Assessment
Assessment includes information gathering, defining the parameters and informing the appropriate personnel in your company on the procedure of the assessment.
2. Identify Exposures
This step includes reviewing the results from the previous assessment (the first step) and rectify the vulnerabilities by forming alternative actionable solutions for your network.
3. Address Exposures
At the final step, an investigation is carried out to determine if there are pregnable services in your IT infrastructure. If such vulnerabilities transpire and if the services are not critical to your business, they should be disabled.
Once these security weaknesses are reaffirmed from the investigation, your company will be informed of any lingering and unpatched vulnerabilities. These need to be rectified and patched by your company to mitigate the risk of a cyber-attack.
How are Penetration Tests Performed? 5
Now that you understand how Vulnerability Assessments are performed, the following 5 steps will briefly describe how a Penetration Test is carried out on your IT infrastructure:
1. Planning & Preparation
The very first step will involve developing clear objectives and scope of the penetration test. The details will include the time, duration and potential impact to your business operations during the penetration test.
2. Information Gathering and Analysis
At this step, a list of potential targets will be formed to be evaluated during the vulnerability assessment. These targets identified are established based on the accessible systems within your IT framework.
3. Vulnerability Detection
Similar to a Vulnerability Assessment, to identify vulnerabilities in your network, penetration testers will utilize manual and automated tools.
4. Penetration Attempt
After performing the third step (Vulnerability Detection), penetration testers would identify suitable targets to begin an intrusive attack to test the system’s defences. All these tests are performed at the within a particular time frame that you have agreed upon.
5. Reporting and Cleaning
Last but not least, a report will be summarised and submitted to you. They include: The Penetration Testing Process; Vulnerability Analysis; Commentary of Vulnerabilities Identified.
You could be worried that these exploitation attempts during tests could affect your IT systems. Do not fret.
To ensure that your accustomed business operations are not affected, the final step will require a complete mandatory clean-up of your systems during the penetration test.
We are sure on what we have shared above have overloaded you with information that could be difficult to digest. Not to worry, here is a quick summary about Vulnerability Assessment and Penetration Testing (VAPT):5
|
|
Vulnerability Assessment (VA) |
Penetration Testing (PT) |
|
Purpose: |
Identify exploitable security vulnerabilities in your IT network. |
Perform actual staged attacks and exploit all vulnerabilities in your IT network. |
|
Type of Reports Provided: |
A list of vulnerabilities that will require patches. The vulnerabilities are sequenced based on its criticality. |
A specific and detailed list of information regarding the data compromised and vulnerabilities exploited. |
|
Characteristic: |
List-oriented |
Goal-oriented |
|
Steps to Perform VA/PT: |
3 Steps:
|
5 Steps:
|
Benefits of VAPT6
We do understand if your company were to invest its money and resources in cybersecurity solutions, there need to be a substantial benefit.
If the above information did not convince completely on why you should fund and conduct such IT security tests yet, consider the following three major benefits that VAPT will bring to your business:
1. Extensive application and data security:
Your business will have the confidence that your internal and external systems, software and applications will be meticulously validated for vulnerabilities.
In addition, VAPT assists your business in constructing more secure applications, improving data security and protecting your intellectual property.
2. Improved compliance standards:
You would have heard of PCI-DSS, ISO/IEC 27002 and other security standards that your company have to oblige due to certain regulations. If you are not in compliance with them, expensive fines could be incurred to your company.
To make this process easier for you, VAPT testing identifies if your IT infrastructure is in compliance with the industry standards and government regulations.
3. Security is built into the process during development:
VAPT provides an efficient and practical method to build secure software, application or program. The primary reason for this is that security is part of the development process.
In the event that your IT network gets compromised, it will require expensive fixes and patches after a vulnerability has been exploited by an attacker. – Wasting unnecessary time, money and resources.
4. Simplify your IT network security
While reading through this blog, you must be wondering, understandably so, how you can manage such complicated cybersecurity solutions. You can see how complex it is to perform VAPT itself.
Here is another issue. If you are always being bombarded with various IT security services and needing to purchase them from different vendors, this becomes a continuous hassle and cost. At Netpluz Asia, we simplify this for you with our managed Security Operations Centre (SOC).
As the popular saying goes, “Prevention is better than cure”. Our SOC can deliver industry-leading tools, technology and expertise to secure your valuable digital assets around the clock at a fraction of the cost. If you wish to find out more about our Managed Security Services, please click here.
Summary
Currently, most enterprises are well equipped with sophisticated and highly efficient security apparatus and software. Hackers are constantly looking for new vulnerabilities to hack into your systems. As a result, cybersecurity has become the most crucial component of any company’s infrastructure.
Vulnerability Assessment is one of the first steps in improving your IT security within your business. When it is executed together with Penetration Testing the two combined operations will create a strong deterrent to cyber-attacks that target your company. Identifying security loopholes and possible damages they can pose are important factors you need to pay attention to when protecting your network from malicious attacks.
This is why many companies have been taking care of their digital assets through VAPT testing. It is an obvious fact that IT security services would incur additional costs for your company, but it is less costly than having your network system partially or fully compromised.
If you wish to find out more information on how you can protect and defend your IT business network through Vulnerability Assessment and Penetration Testing (VAPT), you can visit us at Netpluz 24/7. Alternatively, you may book an appointment by submitting your information here for a free consultation.
Author: Shaun Nisal Peiris
Reference
1 Snow, John, et al. “Top 5 Most Notorious Cyberattacks.” Daily English Global Blogkasperskycom, https://www.kaspersky.com/blog/five-most-notorious-cyberattacks/24506/.
2 Scott Steinberg, special to CNBC.com. “Cyberattacks Now Cost Companies $200,000 on Average, Putting Many out of Business.” CNBC, CNBC, 13 Nov. 2019, https://www.cnbc.com/2019/10/13/cyberattacks-cost-small-companies-200k-putting-many-out-of-business.html.
3 “Vulnerability Assessment and Penetration Testing.” Veracode, 22 Oct. 2019, https://www.veracode.com/security/vulnerability-assessment-and-penetration-testing.
4 Infosec, Cyberops. “What Is VAPT and Why Would Your Organization Need VAPT?” Medium, Medium, 15 May 2019, https://medium.com/@cyberops/what-is-vapt-and-why-would-your-organization-need-vapt-444a684c8933.
5 “Vulnerability Assessment and Penetration Testing.” Cyber Security Agency, https://www.csa.gov.sg/gosafeonline/go-safe-for-business/smes/vulnerability-assessment-and-penetration-testing.
6 Prole, Ken. “Vulnerability Assessment and Penetration Testing (VAPT).” Code Dx, 15 Feb. 2019, https://codedx.com/blog/the-perfect-union-vulnerability-assessment-and-penetration-testing-vapt/.
In this day and age, customers are no longer assessing shopping malls, hotels, and other businesses solely based on their products and services. With internet connectivity being an integral part of our daily life, customers view Wi-Fi access as a necessity and the lack of decent Wi-Fi connection at these commercial areas could in fact lead to poor customer satisfaction.
Based on a study conducted by Purple1, 79.5% of mobile consumers are influenced by the availability of in-store Wi-Fi when deciding where to shop.
Also, Netgear2 surveyed that one in three people travelling for leisure purposes would not return to a hotel with poor internet access. From these two studies, it is evident that the availability of Wi-Fi access is vital to the success of shopping malls and hotels.
Fortunately, with technological advancements in the current digital age, new and enhanced Wi-Fi standards are looking to revolutionise the digital market. Here’s everything you need to know about the 6th Generation of Wi-Fi and why shopping malls and hotels should look to refresh their wireless Access Points.
What is Wi-Fi 6?
Also known as “802.11ax Wi-Fi”, Wi-Fi 6 is the next generation of Wi-Fi technology designed to speed up connections, increase efficiency and also reduce congestion in heavy bandwidth usage scenarios.3 With the introduction of new technologies, Wi-Fi 6 was built to counteract the increasing number of devices in an area and provide better network performance when a number of devices are connected. Aside from providing good network performance, Wi-Fi 6 also provides a more secure Wi-Fi standard for users.
Main Benefits
Faster Wi-Fi Connection
With the launch of Wi-Fi 6, you can now enjoy an explosively fast Wi-Fi connection speed of 9.6 Gbps3, much faster than Wi-Fi 5 (6.9 Gbps)! You may be wondering “What is so special about Wi-Fi 6 that it speeds up the network connection?” Well, there are 2 key technologies that complement one another to support the newly enhanced Wi-Fi 6: MU-MINO and OFDMA.

MU-MIMO, which stands for “Multi-User, Multiple-Input, Multiple-Output,” is a technology that is built in current routers and devices. However, with the new Wi-Fi 6, it allows a router to connect and communicate up to eight devices simultaneously, four more than the previous (Wi-Fi 5) MU-MIMO. It increases capacity, facilitates higher speeds, and is ideal for high bandwidth usage scenarios.4
To provide you with an example, view yourself as a CEO of a small courier company. Previously, your company could only deliver parcels to 4 clients at once due to the limited number of employees. However, after you have expanded your manpower, your company now has the capacity to deliver to 8 customers at the same time. Relating this to Wi-Fi, the upgrade in the Wi-Fi’s MU-MIMO allows fair distribution of bandwidth to eight devices concurrently without affecting the speed of any others.
Another technology that plays a major role in the improved Wi-Fi standards is the Orthogonal Frequency-Division Multiple Access (OFDMA). This technology allows access points to serve multiple devices at the same time.5 For better stability and wider coverage, OFDMA divides its data into smaller sub carriers, and each of these sub carriers will then transmit the intended data to the respective devices.6 This helps to lower its latency which in turn, improves load times and avoid disconnections.7
Here’s another example3 to help you understand better: Imagine your Wi-Fi connection as a convoy of delivery trucks delivering data parcels to your devices. Previously in Wi-Fi 5, each truck could only deliver one parcel to one device at a time. But with OFDMA, each truck can now deliver multiple packets to numerous devices at the same time and thus, increasing the efficiency and speed of completing the deliveries.
Better Security
Aside from network performance, Wi-Fi 6 provides better security for users. Cybersecurity has been a hot topic in Singapore with the various hacking experienced in recent years, one of which is the SingHealth data breach. Fortunately, Wi-Fi has been constantly updating its security and just last year, it has introduced a new security protocol called WPA3. This new protocol provides users with better encryption and authentication8, which increases the protection from password guessing attempts and also, superior security protocols for sensitive data networks9. This tightens security and makes it harder for hackers to crack passwords.10
Here is a summary of the technologies in Wi-Fi 6, and what they can bring to the table:
|
Technology |
Benefits |
|
MU-MIMO |
Connects Up To 8 Devices Simultaneously |
|
OFDMA |
Lower Latency; Improve Load Times |
|
WPA3 |
Better Security |
|
Ignores Neighboring Networks To Prevent Wi-Fi Conflict |
|
|
Improves Battery Life |
How will Wi-Fi 6 benefits Shopping Malls & Hotels?

Shopping Malls
How exactly can Wi-Fi 6 benefit shopping malls in their everyday operation? With Wi-Fi 6’s capability to handle more devices concurrently and provide more overall bandwidth per user without affecting the speed of any others, customers will enjoy a much smoother Wi-Fi connection to satisfy their basic need of accessing the internet even when he/she is in a crowded area.
In addition, Wi-Fi 6 helps lower latency, improves load times and avoids the risk of Wi-Fi disconnection. Imagine your shopping mall experiencing a network failure and everyone is disconnected! Businesses would not be able to operate as usual and customers would not be happy with the service disruption.
All in all, Wi-Fi 6 would definitely help improve the overall shopping experience, potentially increasing customers’ satisfaction and attract new customers. Say goodbye to network congestions and cheers to fast and smooth Wi-Fi connection for your stakeholders with the next generation of Wi-Fi technology!

Hotels
According to 2015 TripAdvisor TripBarometer11, Wi-Fi is the most important in-room amenity for today’s travelers. Likewise, for hotels, guests are actively seeking for Wi-Fi access to participate in online conference calls or sharing content on social media. Given that these activities are heavy in bandwidth usage, hotels should look to refresh their access points. Fortunately, the newly enhanced Wi-Fi 6 has all it takes to provide hotel guests with a better staying experience.
Despite the vast amount of connecting devices, Wi-Fi 6 is able to increase capacity, facilitate higher speeds, and is ideal for high bandwidth usage scenarios. Guests will be able to enjoy streaming videos and participate in video calls without any noticeable decrease in bandwidth quality1.
Furthermore, its new protocol increases the protection from password guessing attempts and also, superior security protocols for sensitive data networks. With the increasing public awareness of personal data theft, concerns of security and privacy are raised more frequently. Wi-Fi 6 ensures a more secured Wi-Fi network to prevent guests’ video calls from being monitored or worse still, having their financial information compromised while making online purchases.11
In summary, Wi-Fi 6 is more than capable to provide hotel guests with a much secure and enjoyable staying experience. Satisfied guests are more likely to introduce their relatives and friends to stay there. These favourable word-of-mouth would potentially bring more revenues to the brand!
Conclusion
Every business is committed in providing the best customer experience. This includes providing fast and reliable Wi-Fi connection during for consumers during their visit to shopping malls and stay in hotels. With Wi-Fi 6, businesses can now battle the increasing number of connecting devices in malls and hotels, providing customers with a better network performance even when in high demand.
Experience a much faster and well-secured Wi-Fi standard now! Feel free to contact Netpluz to learn more about Wi-Fi 6. Alternatively, you may book an appointment by submitting your information here for a free consultation.
Author: Renneth Tan Zi Jun
References
- Majority Of Shoppers Say the Availability Of In-Store Wifi Influences Where They Shop
https://purple.ai/blogs/wifi-influences-where-people-shop/
- Why Hotel Wifi Availability Is Key To Guest Satisfaction
https://socialhospitality.com/2014/08/hotel-wifi/
- Wifi 6, 802.11 Ax, Fastest Wifi Routers
https://www.tp-link.com/us/wifi6/
- What’s the Difference Between Ofdma and Mu-mimo in 11ax?
Anisha Teckchandani
- What is OFDMA (Orthogonal Frequency-Division Multiple Access)?
Margaret Rouse, Laura Fitzgibbons & James Bowen
- Wi-fi 6: What’s Different, and Why It Matters
Chris Hoffman
https://www.howtogeek.com/368332/wi-fi-6-what%E2%80%99s-different-and-why-it-matters/
- What is Wi-fi 6? Here’s a Look At the Next Evolution Of the Wireless Standard
Tyler Lacoma
https://www.digitaltrends.com/computing/what-is-wi-fi-6/
- Why Wpa3 is Necessary To Secure Wi-fi 6 / 802.11ax Networks
James Sanders
https://www.techrepublic.com/article/why-wpa3-is-necessary-to-secure-wi-fi-6-802-11ax-networks/
- Security
https://www.wi-fi.org/discover-wi-fi/security
- Wi-fi 6, Explained: How Fast It Really Is
Jacob Kastrenakes
https://www.theverge.com/2019/2/21/18232026/wi-fi-6-speed-explained-router-wifi-how-does-work
- Why Wi-fi Is Keeping Hotels from Receiving 5 Star Reviews
Carolyn Murphy
https://www.revinate.com/blog/why-wi-fi-is-keeping-hotels-from-receiving-5-star-reviews/
PDPA Compliance – Is Your Corporation’s Data Free From Cyber Threats Such As Data Breaching?
Cyber activities are becoming more common than you think. According to a survey report released by the Cyber Security Agency of Singapore (CSA), there has been a huge increase in cyber threats such as data breach.
Businesses in Singapore suffered losses of around S$58 million in 2018, representing an increase of about 31 percent from 20171.
With the risk of high loss due to cyber threats, this blog article aims to share some simple and cost-effective ways to keep your business safe in the upcoming year.
To begin, let’s first have a basic understanding of the possible cybercrime and its impact.
What is data breach?
In today’s internet world, data breaches are becoming more common for businesses, regardless of the organisation’s size and complexity. Data breach is a security vulnerability where confidential data or sensitive information is released to untrusted websites or misused by cybercriminals. This means that data is at risk of being stolen, transmitted or viewed by unauthorised people outside of your company, which can also be known as a data leak.

How does data breach occur?
Some business owners may think that having a single firewall is sufficient enough to deal with a cyberattack. This mindset increases the attractiveness of the cybercrime industry and provides more targets for attackers to make their profit. A data breach can happen to an organisation in multiple ways such as
Employee Focus attacks: Cybercriminals could send malicious emails that look valid and real to simply request the targeted employees to send in the required details. Employees who have been deceived will unknowingly leak important information that provides hackers with access to all your organisation’s data.
Alternatively, it could be due to sharing of private information to the wrong person. For instance, attaching an important document that contains customer details to someone outside of your organisation who does not have any permission or right to view, and the file can be read by them without any further authentication, like a password.
Malware attack: The data that your organisation owns is very attractive to cybercriminals. To obtain those valuable data, cybercriminals could use malware to hack into your system. One of those is known as Ransomware, which is a malicious program used to acquire a significant amount of data and likely to perform encryption in a single attack. With that, the cybercriminal is able to demand and threaten for payment from the victim in exchange for a decryption key.
Outcome Of Data Breach
Upon data breach, there are many lethal results that could lead to termination of business operation, temporarily or permanently. Data breaches can damage both business and consumers in terms of reputation, which is costly and timely to be repaired. Moreover, businesses may face additional damages in the form of fines or penalties. These consequences may vary due to the type of data breaches and violation of the Personal Data Protection Act.
What is the Personal Data Protection Act (PDPA)?
PDPA is a law that aims to protect all relevant information of an individual such as NRIC, bank account details, among other information against any organisation that is likely to have revealed, collected and used it, despite the credibility of the information. With PDPA, this means that all corporations in Singapore will have to follow a set of baseline standards when managing possession of all individual’s data, even by the firm’s own employees.
How is the PDPA enforced?
The Personal Data Protection Commission (PDPC) has been established to manage and enforce PDPA. The PDPC will determine if a business is not in compliance with PDPA, and the particular company may receive instructions and consequences, such as terminating any collection, use, and disclosure of data in business operations. The company would also be expected to pay fines not exceeding S$1 million.
Protecting against data breach with cybersecurity
With the growth of the internet, there are different security needs such as the application, cloud, mobile, network and endpoint securities. Also, data loss prevention, identify and access management. Cybersecurity is the general IT term to cover different defence remedies and it will allow your corporate to secure the system against any cyberattacks that may lead to data breaches.
Cybersecurity Practices To Mitigate The Risk of Data Breach
These are some easy and effective cybersecurity methods that can ensure that all vulnerable devices, applications, networks, and data in your company’s holding are being protected against any threats.
Secure All Network and Device
This can be done by first installing security software that includes anti-virus and anti-spam filters, which can help your business reduce the possibility of falling for phishing emails and mitigate malware infection.
Also, a firewall could be applied together to track the in and out traffic between all your company computers and the internet. With a firewall in place, the business internal network can be further secured.
Secure With Encryption
Always make sure that your data in files are encrypted in secret code or password when sharing on to the internet. This helps to reduce the risk of data being stolen or destructed online.
Enforce Cybersecurity Policies
By stating out the relevant rules and regulations, your employees can be educated on security issues and things to take note of when they are visiting internet sites or emails.
Conclusion
The right cybersecurity is needed in order to mitigate your corporate’s sensitive data such as financial information, trade secrets or intellectual property of the customers or users. With cyber attackers and hackers becoming more prominent and creative it is difficult to acquire an effective solution. Not to worry! At Netpluz, we have partnered with leading cybersecurity vendors such as Nexusguard, Sophos, Druva and many more that can provide a variety of cybersecurity solutions that can help your company reduce the negative impacts of data breaching and at the same time save cost.
Click here to find out more about ways to defend your data, or email us to arrange for an appointment with our experienced manager, and we will provide ways for you to become more secure.
Author: Ada Foo Jiaxin
References
1 CISOMAG. “Around 6,200 Cyber-Attacks Reported in Singapore Last Year: CSA.” CISO MAG | Cyber Security Magazine, 20 June 2019, www.cisomag.com/around-6200-cyber-attacks-reported-in-singapore-last-year-csa/
Irwin, Luke. “The 6 Most Common Ways Data Breaches Occur – IT Governance Blog.” IT Governance Blog, 11 Mar. 2019, www.itgovernance.eu/blog/en/the-6-most-common-ways-data-breaches-occur.
“What Is Cyber Security Threat Mitigation? Webopedia Definition.” Webopedia.Com, 2019, www.webopedia.com/TERM/C/cyber-security-threat-mitigation.html#:~:targetText=Cyber%20security%20threat%20mitigation%20refers,when%20security%20attacks%20do%20happen.
What is Cybersecurity (Cyber Security)? Everything You Need to Know. “What Is Cybersecurity (Cyber Security)? Everything You Need to Know.” SearchSecurity, 2019,
“How to Protect Your Business from Cyber Threats | Business.Gov.Au.” Business.Gov.Au, 15 Oct. 2019, www.business.gov.au/Risk-management/Cyber-security/How-to-protect-your-business-from-cyber-threats.
STABILITY OR SECURITY: MAKE THE RIGHT CHOICE BETWEEN STATIC IP AND DYNAMIC IP
Business Internet Connectivity
It has become common for businesses like yours to be bombarded with broadband packages from various Internet Service Providers (ISP). Customarily, you will have to make a decision in selecting either a Static IP vs. Dynamic IP (Internet Protocol) business broadband for your internet access.
In spite of your company’s size and scope, you need to determine what the most pragmatic approach should be in selecting your company’s IP. Should it be Dynamic IP or Static IP? This blog will provide you with all the know-how regarding your IP selection so that you can make a well-informed and clear decision.
Static and Dynamic IP Explained
By definition of the words, Static and Dynamic imply something that is, respectively, fixed or constantly changing.
A Static IP will be configured manually by your ISP. They will assign a permanent IP address to a particular device you want to connect so that your devices will use the same IP address when connecting to the Internet. This assigned address remains unchanged until your business has deactivated the device or changed the overall framework of your network.
On the other hand, Dynamic IP will not be configured manually by your ISP. Instead, whenever your device is restarted, a new IP address will be assigned by your ISP’s Dynamic Host Configuration Protocol (DHCP) servers. Your device will sort of “lease” an IP address to get connected. This means that temporary IP address assigned by the DHCP servers will periodically change when each device connects to the internet. 1
Here’s an easier illustration to see how a Static and Dynamic IP would typically operate:
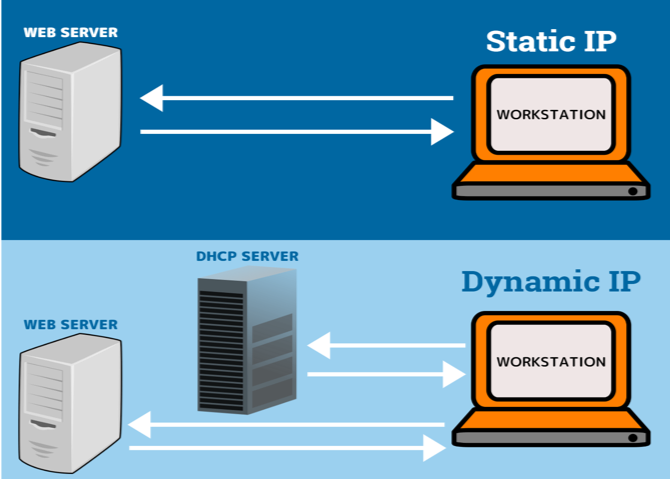
What are the differences?
Both Static and Dynamic IP will eventually provide you with an IP address to enable your device to communicate with others over an IP-based network. So you might be wondering, what are their differences? To give you a more comparative analysis, here are the 5 key components that differentiate Static and Dynamic IP.
|
|
Static IP |
Dynamic IP |
|
IP address: |
Does not change – Permanent IP address |
Changes Dynamically – Temporary IP Address |
|
Assignation: |
Assigned by the Network Administrator |
Assigned by the DHCP Server |
|
Configuration: |
Configured Manually |
Configured Automatically |
|
Sharing: |
IP addresses cannot be shared or used by any other device |
IP addresses can be shared |
|
Conventionally used by: |
Financial institutions and large corporations. – Used for dedicated servers. |
Private sector and residential areas – Used for connecting large network to the internet |
When should you opt for Static or Dynamic IP?
Google has stated that most users do not require static IP addresses in general.2 Dynamic IP is known to be the more popular option as they are undemanding and cheaper to deploy.3
Does this mean that Dynamic IP is the way to go? Well, not really. In fact, businesses would be more suited for a Static IP than residences. A Static IP will matter more if your external devices or websites need to remember your IP address.
Also, it is worth noting that internet connectivity can vary based on the nature and needs of your business. The benefits of Static and Dynamic IP that we share in this blog, will equip you with vital information in making an informed decision solely based on the benefits that your company could reap according to your business needs.
Opting for Static IP
According to Frontier Business there are three predominant reasons why your business should opt for a static IP.4 This is typically when your business:
- Hosts servers or websites – Including mail, File Transfer Protocol (FTP) and Virtual Private Network (VPN) servers
- Utilizes Voice over Internet Protocol (VoIP) or other digital voice services.
- Often permit employees to work remotely.
Although all the businesses do not operate based on the 3 points mentioned above, Static IP could still be important to your business.
To allow you to identify if it will suit your company’s internet connectivity needs, here are the 3 key benefits that Static IP will bring to the table:5&6
- Better Stability
- Faster Data Exchange
- Convenient remote access
1) Improved Stability
As we have previously mentioned, a Static IP address will never change. Which is why it is known to have a more stable Internet. If your IP address were to change on regular intervals, let’s say every few hours, this could eventually cause a lapse in your internet connection. Furthermore, your devices might also have trouble reconnecting to the Internet given its new IP address.7
This is when a Static IP comes in handy. If your business relies on Voice-over phone systems (like VoIP) and applications that require broadband services to communicate, Static IP will deliver a more superior connection that is reliable.
2) Faster Data Exchange

If your business requires downloading and retrieving files at breakneck speed, the Static is the ideal IP to have8 because static IP addresses provide you with faster upload and download speeds.
Considering its inherent reliability on the internet, file transfers are easy and reliable, and data can be sent and received promptly.
3) Convenient Remote access

The extensive advancement in networking technology has made it easier than ever for employees to work from home. Your employees just need to connect their devices to your IP address to access their devices remotely at any place, anytime. This also includes your VPN or other remote access programs as they remember your static IP address.
Opting for Dynamic IP
Since we understand the nature of Static IP, under which circumstances do we need to select Dynamic IP? It is relatively simple decision to make as long as you have the company’s desired goals on your mind. If you don’t use or plan to use any of the above technology or processes, a Dynamic IP for your business internet would be the way to go. Just like the Static, Dynamic will also have its own inherent set of benefits.
Here are the 3 main benefits that a Dynamic IP will bring to your business if you were to opt for it:5&6
● Better Security
● Lower Cost
● Unlimited IP addressing
Improved Security

As we have stated earlier, Dynamic IP address never remains the same. The address changes on each and every session when a device connects to the internet.
The advantage of Dynamic IP is that it will make the process harder for a potential cyber attacker to find where exactly you are situated in the network. This mitigates the cybersecurity risks by letting hackers look elsewhere instead of targeting your network, software and hardware.
You can also add an additional layer of security by masking your network address with a VPN.
Lower Cost

We understand that investing more than it requires on your internet needs is the last thing you want to do. The good news is that your ISP does not incur additional fees when you opt for a Dynamic IP address
Well, why does your ISP charge you a lower price?
Typically, your ISP’s DHCP server will assign an available IP address from a pool of reusable IP addresses to your device.9 Since your ISP would not have to purchase these IP addresses to “reserve” a particular address in the network, the cost will be reduced.
Unlimited IP Addressing

Dynamic IP will render unlimited IP addresses as it allows you to reuse un-utilized IP addresses. If you own a business that requires changing of devices or installing new ones occasionally, you may need to pay more attention to the choices you would make.
If you were to connect a device to your network, you do not need to manually disconnect the old IP address and assign a new one. This will ensure that two devices won’t be in conflict with one another on the network when using identical IP addresses.
As we have mentioned previously, the DHCP server (or router) will take care of this perpetual process automatically for you.
Summary – Static or Dynamic IP?
There are many comprehensive broadband plans available in today’s technology market. It is needless to say that selecting the most ideal internet connectivity plan plays a major role in the success of your company.
Based on the information provided in this blog, we can see both the Static and Dynamic IP bring certain benefits to your business.
Here is a quick summary of the benefits of Static IP and Dynamic IP:
|
|
Static IP |
Dynamic IP |
|
Improved Stability |
✔ |
|
|
Faster Data Exchange |
✔ |
|
|
Convenient Remote Access |
✔ |
|
|
Improved Security |
|
✔ |
|
Lower Cost |
|
✔ |
|
Unlimited IP Addressing |
|
✔ |
While Static IP provides the stability, ease of data exchange and remote access to businesses that host websites and/or internet services, Dynamic IP, on the other hand, brings about more affordability and security on the internet. These two factors needed to be taken into consideration when selecting an IP.
If you wish to find out more information on Static IP, Dynamic IP or other broadband services, you can visit us at Netpluz. Alternatively, you may book an appointment by submitting your information here for a free consultation.
Author: Shaun Nisal Peiris
References
- Iplocation.net, https://www.iplocation.net/static-vs-dynamic-ip-address.
- “Static vs. Dynamic IP Addresses.” Google Fiber Help, Google, https://support.google.com/fiber/answer/3547208?hl=en.
- “DHCP vs Static IP: What’s the Difference?” Blog, 1 Aug. 2018, https://community.fs.com/blog/dhcp-vs-static-ip-differences.html.
- “Static vs. Dynamic IP-Find Out Which Is Right for Your Business.” Frontier Business, 7 May 2019, https://business.frontier.com/blog/static-vs-dynamic-ip/.
- “Static vs Dynamic IP: What Do You Really Need?” Udemy Blog, https://blog.udemy.com/static-vs-dynamic-ip/.
- Vaughan-Nichols, Steven J. Static vs. Dynamic IP Addresses, Avast, 31 Oct. 2019, https://www.avast.com/c-static-vs-dynamic-ip-addresses#topic-3
- Kurin, James, et al. “The Advantages & Disadvantages to a Static IP Address.” Techwalla, https://www.techwalla.com/articles/the-advantages-disadvantages-to-a-static-ip-address.
- Hayes, Brooke. “Dynamic vs. Static IP Addresses.” Business.org, 13 Aug. 2019, https://www.business.org/services/internet/dynamic-vs-static-ip/.
- “Blog.” Image, https://www.pacificinternet.com/en/blogs/115-blog10.html.
The Difference Between Public VS Private Cloud
Businesses are transforming more application are moving into the clouds.
Gartner predicts that by 2021, businesses will adopt an all-in cloud strategy.
When businesses start to use SaaS (Software as a Service), IaaS (Infrastructure as a Service), PaaS (Platform as a Service), and FaaS (Function as a Service), the company must adapt and design their own network architecture in order to be secure.
When businesses are moving to the cloud, it means that they are having a data centre made up of compute and storage resources connected by network somewhere. When you are considering cloud computing solutions for your business, it is better to learn the difference between the types of clouds that you’re going to choose in order to maintain your own secure network architecture.
Nowadays clouds are smart, automated and adaptive. Migrating from the traditional data centre to clouds might improve the efficiency and reduce the cost for your business.
There are two categories of clouds for a growing business, private and public cloud. Public cloud run by the cloud service provider that rent their space for their customers, usually small businesses that only pay as they are using the services. While private cloud usually used by a big enterprise to have their own control in the term of management and customization.
In term of storage and access, public cloud will give access to multiple organizations and will store your data on a shared infrastructure, while in private cloud, your company can have restricted access at a time and dedicated storage infrastructure that is not accessible for others
Using public cloud means that the location of the data centre varies by the public cloud provider’s infrastructure site, while private cloud allows the company to have the freedom to decide and choose, an on-premise data centre or dedicated location on the service provider’s infrastructure.
Having private cloud as your cloud computing solutions might require additional investment for hardware components while on the other hand, public cloud is easy to deploy as they usually do not require additional investment for either hardware or software. The additional investment might cause a company to spend more on hardware to set up on-premise data centres to leverage private cloud services efficiently while using public cloud can help business reduce cost as the company will not need to install anything.
Even if the public cloud is less expensive than private as there is no additional cost, Public cloud has disadvantages when it comes to management, customization and control over the cloud which could be an issue for lack of security.
When a company uses a public cloud, all the data stored in the provider’s data centre and cloud provider is responsible for the management and maintenance process. Having a private cloud give the company more control when it comes to managing their own cloud as they have dedicated administrator to manage the upgrades and installations and this makes it easy to integrate their on-premise or on-cloud applications.
Having a private cloud allows companies to customize their cloud infrastructure according to their business-specific needs and requirements, while the public cloud-only offers a standard operating procedure for organizations.
For scalability, the public cloud offers additional space and infrastructure abilities for their customer and private cloud not only could give incremental space and infrastructure abilities but also offer the customized scalability.
In terms of security, private cloud holds the advantage as all the data and cloud is controlled by a dedicated administrator in a company. Management of private cloud can be customized and enhanced to implement higher levels of authentication and security for the cloud environment.
This power to control the cloud environment helps the company to easily add and remove users and have a strict policy on who can access which data and what the users can do inside the cloud. While easy to deploy public cloud can only have standard security protocols that controlled by the cloud provider.
While big enterprise might opt for a private cloud and small business prefer to go with a public cloud, there is also a solution to have the best of both cloud, which is a hybrid cloud. Hybrid cloud can be the solution for a company that wants to remain their network environment secure by having the most sensitive applications in the private cloud while storing the other forms of applications in a public cloud service provider.
If you are having a problem to decide which cloud environment that suitable for your business model, you can contact Netpluz for a free consultation on your cloud computing needs. Netpluz is MTCS SS 584 compliant. Our team have a commitment to ensuring sound operational and security control across all computing services.
The Multi-Tier Cloud Security (MTCS) Singapore Standard (SS)584 is a cloud security certification managed by the Singapore Info-comm Media Development Authority (IMDA).
The MTCS SS is the world’s first cloud security standard that covers multiple tiers. With the new standard, certified CSPs will be able to spell out the levels of security that they can offer to their users.
Businesses that rely on cloud computing services will also be able to use the MTCS SS to better understand and assess the cloud security they require.
IS SD-WAN RIGHT FOR MY BUSINESS?
SDWAN (or SD-WAN) stands for Software-Defined Wide Area Network is gaining popularity among business, especially those who require simplicity in expanding their connectivity across their regional offices or branches. Most have heard of the term but is still unsure how it will deliver or even the benefits of embarking on such a project.
The reasons are very simple!
SDWAN is an automated approach to business or enterprise network connectivity, both locally and regionally, and allows optimisation of network performance leveraging on Software Defined Network (SDN) technologies.
SD-WAN, according to Wikipedia, is defined as “an acronym for software-defined networking (SDN) in a wide area network (WAN).” The page also stated that SD-WAN simplifies the operational management of Wide Area Networking by separating the networking hardware such as traditional routers from its control mechanism.
So do I really need SD-WAN?
One of the biggest push factors of SD-WAN adoption is the cost to deploy, reliability of service and security level. The top and main goal of SD-WAN technology are to deliver a business-grade, secure yet simple cloud-based and cloud-enabled WAN connection with as much open and software-based technology as possible, according to an article posted at SDX Central .
The main reason on why so many businesses turn to SDWAN is because the concept and successful case studies proved that SDWAN simplifies the business network management administration, and it is a whole lot easier to manage than traditional and legacy WANs. This is done by moving the network management to the cloud. To simplify this statement, you are no longer going to rely on physical network management all the time but with SDWAN, you will leverage on a combination of network paths and routing, through the cloud, like most new virtualised technologies. Remember the time when virtualisation was the hottest topic in the market?
To summarise this even further, SDWAN is going to be very useful and massive stress reduction to your Information Technology (IT) team to manage your multiple offices, branches or locations, both locally and regionally. Your team will be able to enjoy, under a single pane of glass with improved Quality of Service (QoS), on network-wide control and visibility. The platform is powered to connect and communicate with all network endpoints without the need for additional or extra technology, protocols or an IT engineer on-site to reconfigure.
Imagine this, with the addition of new protocols, IT engineers often need to manually update each endpoint and this will often lead to human error, causing downtime and possible loss of potential revenue. With Cloud-based and managed, every update can be done from the cloud, potentially and significantly reduce error, save time and cost reduction. One of the major benefits of SD-WAN is the simplicity and time required to set the solution up and running for your business.
Extensive hardware that traditionally requires a lot of effort and long lead time can now be tested, deployed and provisioned in a matter of business days, and no longer weeks or months.
Sounds interesting?
Hold your horses! There are things to consider!
Even though there are a lot of benefits that will entice you to get onboard SDWAN, there are still a number of factors and considerations to keep in mind and discuss with experts when you are deciding whether to deploy SD-WAN solution for the business and how to proceed further.
For instance, would you consider to manage SDWAN in-house or do you want it delivered by a Managed Service Provider, under SDWAN-as-a-Service? Compared to managing it in-house, getting it delivered through managed service can be much faster to deploy and less hassle. This would mean that there will not be a need to hire additional skillset, in most case, very expensive skillset to manage such a platform. The managed service provider, Netpluz can support local and regional deployment, manage for you as a service, so ultimately it will be more convenient.
Another consideration will be if you are planning to use an internet-based SDWAN setup deployment or a global private network for security purpose. Internet-based, such as the use of readily available fibre broadband internet connectivity might be good enough for your business if your offices or branches are based locally, and the internet is of high reliability and quality, such as in Singapore.
However, it could bring issues for global deployment of SDWAN if you are looking into setting up a global private network that provides faster response time and increased security level. Interested parties often ask if SDWAN is a replacement for Multiprotocol Label Switching (MPLS). If you have not read our blog on SDWAN vs MPLS, you can click here to read more. The answer may surprise you.
SD-WAN technologies are taking off like an upward rocket mainly due to their ease of management and the higher levels of network optimisation and automation they deliver. Despite this, 80% of enterprises have chosen managed SD-WAN, as compared to 20% choosing to deploy SD-WAN in-house route according to recent research by Frost & Sullivan.
So which path should I be heading towards?
There is no single way to manage SD-WAN. Businesses must carefully map out which road works best for them when it comes to deploying and managing SD-WAN, taking into consideration their business needs and growth path in the upcoming 3-5 years. This is why Netpluz can come in to consult with you, show you a LIVE DEMO on the SDWAN solution, to help you in your evolution and digital transformation to SDWAN.
You might also be interested to read up an ebook on SDWAN for dummies guide that was published by our selected SDWAN partner, Velocloud, now part of VMware. You can download the ebook by clicking here.

Netpluz is a registered partner of VeloCloud.
What happened recently with so much Data Breaches news coverage?
One of the key challenges for organisations today is how to safeguard their information systems and digital infrastructure from attacks by malicious hackers and cybercriminals. Current concerns for most companies are often related to data breaches, with so much media coverage focusing on recent cases.
In light of recent data breaches discovered on Singtel and Ninja Van, Personal Data Protection Commission (PDPC) mentioned:
“Despite having received professional advice to take precautions against such vulnerabilities, the organisation omitted to conduct a full code review…and hence failed to discover (the vulnerability) that was exploited in this case.”
No matter how certain organisations are about their defences, there are always risks to their security because of frequent changes and updates made to their digital infrastructure.
Due to these issues, vulnerability assessment and penetration testing (VAPT) come in place as a solution to identify the unknown vulnerabilities and set immediate remediation to mitigate cybersecurity risk for the company.
According to PDPC, eight organisations were found to be in breach of the Personal Data Protection Act (PDPA).
- Ninja Logistics for failing to put in place reasonable security arrangements to protect customers’ data in relation to a tracking function on the company’s website, allowing the data to be accessed publicly.
- EU Holidays, penalty of $15,000, for not protecting customers’ personal data and not having written policies and practices to comply with the PDPA.
- Marshall Cavendish ($40,000), Singtel ($25,000) and SearchAsia Consulting ($7,000); and a warning issued to another two – Tan Tock Seng Hospital and CampVision.
- Directions were also imposed on iClick Media for breaching the Accountability Obligation.
Is Your company ready for Vulnerability Assessment & Penetration Testing (VAPT)?
Vulnerability Assessment & Penetration Testing (VAPT) is necessary to spot your vulnerability. VAPT result shall deliver quality assessment through the eyes of both a hacker and an experienced and certified security expert to discover where you can improve your security posture.
The findings (vulnerabilities) would be delivered as reports that shall be used to effectively remediate any of the vulnerabilities and answer these following questions:
- How vulnerable are you from the internet or intranet?
- What are the exploitable vulnerabilities?
- Are the operating system patches current?
- Do you have unnecessary service running?
“Knowing your vulnerability and the way in which the attackers could exploit them are one of the greatest insights you can get in improving your security program.”
Want to know how we can help you discover vulnerabilities through VAPT?
Reference
Singtel fined $25,000 and Ninja Van $90,000 for data breaches, The Strait Times, Nov 5, 2019. – https://www.straitstimes.com/business/companies-markets/singtel-fined-25000-and-ninja-van-90000-for-data-breaches
New Commission’s Decisions on 4 November 2019, PDPC, Nov 4, 2019 – https://www.pdpc.gov.sg/pdpc/news/latest-updates/2019/11/new-commissions-decisions-on-4-november-2019
7 alarming factors that could cost your company thousands of dollars if you make this one fatal mistake: Debunking the myth between SD-WAN and MPLS
“SD-WAN is sure to be better than MPLS…” We have heard it many times from people claiming that software-defined networking in a Wide Area Network (SD-WAN) is better than Multiprotocol Label Switching (MPLS) in the area of managed services.
However, is it really true for your business?
MPLS has always been competing against SD-WAN solutions to meet today’s high demands and expanding needs for networked-critical systems. In reality, there are more to these claims than meets the eye. In this article, we will compare the pros and cons between these 2 network technologies and you will then be able to discover whether SD-WAN is actually good for your company.
What is MPLS?
MPLS is a traditional network technology that forwards data for network traffic and directs data through a path via labels. This helps to eliminate the need for complicated lookups in a routing table at every stop and a label is assigned to each packet to differentiate itself from other traffic on Wide Area Network (WAN). 3
What is SD-WAN?
SD-WAN is a networking technology that uses software to make wide-area networks more intelligent and flexible by connecting sites directly to the internet over commodity broadband links. This helps to eliminate the need for administering each WAN device manually. It is being done through the use of managing configurations centrally and access policies. 3
If you want to find out more about everything you need to know about SD-WAN, do read up another blog on it by clicking here.
MPLS VS SD-WAN: The 7 deadly factors that will cost your company a lot if you don’t make the right choice in selecting the right technology
Bandwidth
MPLS comes with a high bandwidth cost. It is not suitable for high bandwidth that is above 100m as its circuit cost is expensive. MPLS requires a huge amount of effort to add new links as compared to SD-WAN. Thus, MPLS is not recommended for companies with branch offices, remote sites and those who need to grow their distributed network capabilities quickly. Unlike MPLS, SD-WAN comes with zero bandwidth cost through the use of many, high-bandwidth and cheap Internet connections simultaneously. Customers are able to upgrade with ease by adding new links without causing any changes to the infrastructure or the network. Through this process, your company will then have an inexpensive internet connection without sacrificing its performance. 1, 2
Performance
MPLS can only send traffic via one network connection and that the settings of your class of service cannot be changed. Thus, resulting in low speed at which the traffic is being sent. However, SD-WAN will help to control unimportant traffic while sending the rest of the traffic via the fastest route across the internet circuit. Therefore, with only the important traffic being sent across the fastest route, it will enable SD-WAN to perform at its highest performance. 1
Uptime
MPLS will have a failover to a substitute internet connection. However, you will experience some delay during the failover most of the time; which will decrease the uptime on MPLS for your company. Unlike MPLS, SD-WAN can allow your company to aggregate many ISP Internet and Wide Area Network (WAN) at a single site. Thus, your company will not have any circuit redundancy for your WAN which will increase uptime for your company. 1
Performance independent of geographical location
MPLS does not have a network for companies in a remote or international location. As a result, those companies will have an underperforming network as they run all traffic over an IPsec VPN. However, the benefits that SD-WAN provides for your company will never change, regardless of the underlying ISP your company is using. This is done through the use of switching transport for businesses. The cable or wireless infrastructure that connects the branch offices and data centres allows the company to mix and match them based on bandwidth availability. It will then quickly and easily spin up new connections to remote locations. Therefore, there will not be any underperforming network when using SD-WAN regardless of your geographical location. 1, 2, 5
Reliability and quality of service
MPLS is able to deliver packets reliably and provide a high quality of service. It also creates the quality of service buckets that ensure high priority traffic being delivered with minimum packet loss; this helps the system to operate without any loss of signal or quality over an MPLS framework. Thus, this network is significantly important for companies that rely on real-time protocols such as VoIP, virtual desktops and video conferencing. However, SD-WAN still connects your sites using the public internet which will carry a high amount of data loss risk. As soon as the packets reach the public internet, it is very difficult to ensure a low level of packet loss, latency and jitter which will definitely cause real-time applications to fail. These lost packets will ultimately cause congestion which will result in a time out. 2, 3, 4, 6
 |
 |
| Without SD-WAN @ 2% Packet Loss | 2% Packet Loss with SD-WAN |
High predictability of traffic
As each packet is assigned with a label, MPLS is able to separate it from other traffic on the Wide Area Network. When a label is being assigned to each packet, MPLS providers can then assign different priority to certain network traffic. These benefits, which are derived from the assigned labels to individual packet, will help to bring predictability of traffic to a network. 3
High level of Security
SD-WAN is heavily invested in security as it integrates security, policy, and orchestration of network architecture. All network, which includes the internet, that is sent in SD-WAN architecture are encrypted. All devices and endpoints are completely authenticated through the use of a scalable key-exchange functionality and software-defined security. Therefore, with the help of the encryption of information and the scalable key-exchange functionality, the security of SD-WAN network is enhanced. 3, 5
This table shows a summary of the respective features that MPLS and SD-WAN provide.
|
Feature |
MPLS |
SD-WAN |
|
Increased-Bandwidth |
X |
✓ |
|
Increased Performance |
X |
✓ |
|
Increased Uptime |
X |
✓ |
|
Performance independent of Geographical location |
X |
✓ |
|
Reliability and Quality of Services |
✓ |
X |
|
High Predictability of Traffic |
✓ |
X |
|
High Level Of Security |
X |
✓ |
So which should I choose for my company: SD-WAN or MPLS?
With SD-WAN technology offering more benefits than MPLS, companies may choose to take up SD-WAN technology. From its inexpensive cost to flexibility to easy of linking and to the increased security that SD-WAN offers, the benefits of SD-WAN is really obvious.
No wonder, many have claimed that SD-WAN is better than MPLS but does that necessarily mean that it is better for your company?
The answer is No.
Why? The reason is simple; many businesses may choose to take up SD-WAN than MPLS as they are trying to make their WAN infrastructure more efficient and evolve towards more cloud-based applications. Now, this means that if your company is using the cloud, SD-WAN would definitely be a better choice than MPLS.
However, if your company relies heavily on mission-critical, real-time applications running over the WAN such as phone calls, video conferencing and remote desktop, MPLS would be a better choice for your company.4
In summary, if your company is more suited for MPLS but you choose SD-WAN instead or vice versa, then that is the number one fatal mistake that will cost your company tons of money.
If you are still confused or unsure to choose between MPLS or SD-WAN, you do not have to worry or be frustrated!
Here at Netpluz, we provide free consultation and LIVE DEMO to better decide which network technology is best for your company. Click here to contact us for a free consultation!
Author: Chua Yi Run Stace
References
- Smith, Mike C., and IDG Contributor Network. “Is SD-WAN Better than MPLS?” Network World, Network World, 21 Sept. 2017, www.networkworld.com/article/3226371/is-sd-wan-better-than-mpls.html.
- Connor Craven. “SD-WAN vs MPLS: The Pros and Cons of Both Technologies” SDxCentral, 24th July 2017, https://www.sdxcentral.com/networking/sd-wan/definitions/sd-wan-vs-mpls-pros-cons-technologies/
- “SD-WAN vs MPLS” , Forcepoint, https://www.forcepoint.com/cyber-edu/sd-wan-vs-mpls
- “SD WAN vs MPLS: Pros and Cons”, FS.Com, 26th Jul. 2018, https://community.fs.com/blog/sd-wan-vs-mpls-pros-and-cons.html?c_site=w_site
- “The Primary Benefits of SD-WAN Technology” , SDxCentral, 27th Jun. 2017, https://www.sdxcentral.com/networking/sd-wan/definitions/sd-wan-technology/
- Rivenes, L, “What are the Causes of Packet Loss?” Datapath.io, 8th Mar. 2016, https://datapath.io/resources/blog/cau
5 Benefits Why You Should Engage a Managed IT Services Provider
Why should any company engage a managed IT services provider?
In this article, we will discuss five benefits for your company, including improving your own company’s IT productivity, which will in turn drive down your overall company’s cost.
But first… what is managed IT services?
In simple terms, managed IT services is a comprehensive solution that is delivered by an IT service provider. These services include set-up, maintenance, remote support, proactive support, monitoring, reporting and advisory services for your improvement.
Top 5 Benefits of engaging a Managed Service Provider (MSP)
-
Internal IT vs MSP
A company may have only one (or a few) internal IT staff who is responsible for all the technical duties regarding the company. This person will need to take charge of technical duties such as troubleshooting, dealing with connectivity issues and replacing or configuring hardware and software. When the staff is engaged or not around, the company will be left helpless if something goes wrong. Whereas when your company has a managed IT services provider, you acquire access to an entire team of IT experts who are well skilled and have diverse skill sets. There will be someone to rescue you at all times as managed service providers offer better resources, and companies enjoy the benefit of multiple people working on multiple issues simultaneously. You can think of this as being entitled to an IT manager and a virtual CIO!
-
OPEX vs CAPEX
Capital expenditures called CAPEX reflect expenses that an organisation incurs for future benefits. For example buildings or machinery that depreciates over the years, with the annual depreciated amount being deducted from the company’s revenue in the income statement. On the other hand, operating expenses called OPEX are day-to-day expenses incurred such as wages, office supplies and leases. Thus, OPEX is deducted fully from revenues in an income statement. Businesses are also taxed based on revenues minus all OPEX.5,6,7
For IT matters, owned hardware such as switches or phones are typically classified as CAPEX. Hardware may require huge capital outlays upfront, with the equipment’s lifespan determining its annual depreciation. Software, cloud applications or rented hardwares are categorised as OPEX.
To find out which is preferred, often the finance department prefers OPEX as it reduces the company’s owed income tax. Another disadvantage of CAPEX is that it may require multiple layers of management approval. Therefore, companies these days prefer having OPEX rather than CAPEX.7
-
One-stop Managed IT Services
By engaging a managed service provider, you will be entitled to a one-stop solution provider by an IT service provider. The managed service provider takes full charge of IT consultation, network management, server administration, data backup, virtualisation and devices recommendations. For example, Netpluz Asia is also a one-stop managed communication service provider that offers reliable and high-performance communication services such as data, voice, video, cybersecurity, mobility and analytics needs. Hence, by engaging Netpluz Asia, you are assured of getting assistance from IT experts that will give you peace of mind.4
-
Price
Typically, the price is lower when engaging a managed IT services provider as the comprehensive solution provided will be catered to your own needs. You will not need to pay for services not required by the company. However, when there are multiple vendors involved in managing your company’s IT matters, the price will definitely be higher. This is due to the separate individual vendors that will be offering separate and smaller service packages – and you don’t enjoy the benefits of a bundled package. To refrain from making these extra expenses, you can engage a managed IT services provider such as Netpluz to save cost.
-
Complexity
When your company is managed by multiple IT vendors, your company will be responsible for overall integration as each vendor is responsible only for their individual product. Even if they are able to do so, it will be at a higher cost.1 However, managed service providers give you the benefit of a cohesive package and integration of the various services. You also enjoy the benefit of a one-stop provider and single point of contact despite the variety of systems deployed.
You avoid the risk of multiple vendor pointing fingers at each other when something goes wrong.
Conclusion
Your company will certainly be at an advantage compared to companies that are still engaging multiple IT service providers or better still those companies that are relying on their IT staff or separate vendors. Most importantly, your managed IT service provider will be able to monitor and maintain your company’s IT environment, enabling the prevention of network problems before these turn into downtime that usually comes with a huge price tag.
Your one-stop managed IT service provider is only a website away. Click on this link https://www.netpluz.asia/ to learn more about how Netpluz can show you the benefits of a managed IT service provider.
Author: Shiva Shanthini d/o Murugesen Pillai
References
1.Henry Cheang. “Single vendor vs. mutli-vendor: 8 factors to consider.” Cimpl, June 4, 2014
https://blog.cimpl.com/single-vendor-vs.-multi-vendor-8-factors-to-consider
2.Anastasia. “The Benefits of Outsourcing to Managed Services.” CLEVERISM, July 9, 2019
https://www.cleverism.com/benefits-of-outsourcing-to-managed-services/
3.By User. “CHOOSING BETWEEN AN MSP VS. INTERNAL IT DEPARTMENT.” CitadelBlue, January 3, 2019
https://www.citadelblue.com/choosing-between-an-msp-vs-internal-it-department-2/
4.“One-stop Managed IT Service.” IT Solution
https://www.itsolution.com.sg/it-services/one-stop-managed-it-services/
5.“Capex vs Opex.” WallStreetMojo
https://www.wallstreetmojo.com/capex-vs-opex/
6.Christina Majaski . “The Difference Between an Operating Expense vs. a Capital Expense.” iInvestopedia
April 14, 2019
7.“Capex vs. Opex.” Diffen
https://www.diffen.com/difference/Capex_vs_Opex
Everything you need to know about SD-WAN: The top 3 benefits of using this next generation technology for digital transformation

What is SD-WAN?
With businesses shifting towards the age of digital transformation, SD-Wan is emerging as the next generation of networking solutions. But what exactly is SD-WAN?
SD-WAN is a cost-effective alternative to the traditional networking technology which is used to effectively connect the network of several locations from different geographical locations. To illustrate this, think of it as the tracks that connect all the train stations. Here are some of the benefits that SD-WAN brings to the table:
- Cost reduction
- Better security
- Minimise downtime

Cost reduction
Firstly, SD-Wan saves cost by preventing productivity losses. Every data packet that is sent will travel through the path of least resistance across the network. This ensures that the data will reach as quickly as possible and allows critical applications to have the best performance.
Furthermore, it also comes with prioritising capabilities – an employee browsing the Web during lunch hour will not take priority over a staff member making an important call to a business partner. The increase in performance will prevent costs from lost productivity.1
Lastly, the flexibility of SD-WAN helps save cost by allowing organisations to utilise network resources more wisely by not paying for unnecessary bandwidth. They can alter bandwidth based on their requirements without having to wait for the IT team to be physically present. The upfront costs of SD-Wan are also extremely low as there is no physical equipment required.2
To illustrate further, let’s have a look at Kindred Healthcare. The healthcare company needed to create a secure zone for the prevention of corporate network traffic from interfering with their clinic’s network traffic.
Due to having a small team to manage connections across 700 sites, the company started using SD-WAN and the results were mind-blowing. The company increased its bandwidth by up to 700% and saved 4 million dollars over 5 years.6

Better Security
SD-WAN improves network security through the encryption of WAN traffic as it travels from one location to another. This ensures that if a breach occurs, the network will be segmented to minimise the damage caused.3
Next, SD-WAN clearly shows the information on the amount and types of traffic on the network. This enforces better security by assisting IT administrators in detecting attacks more quickly.
Moreover, it is also easily accessible by employees and partners of the organisation without being vulnerable to cyberattacks. This comes with security features such as firewalls, intrusion prevention and URL filtering. Organisations will not have to worry about a breach in security using key software applications when they are in public areas such as coffee shops or airport lounges.4
SD-WAN is also able to integrate with a cloud web content filtering service which offers malware defenses and botnet command-and-control intervention for every branch and remote devices.5
For instance, Exxon Mobil needed an easy and secure way to connect over 10,000 locations, which ranges from retail sites, wholesalers to wholesaler branches. The switch to an SD-WAN model allowed the locations to use their broadband, 3G or 4G connectivity. All these were done with the enforcement of strict security policies, especially when it came to credit card security.
The solution Exxon Mobil needed also had to be able to deploy multiple types of networks for different purposes. SD-WAN allows each network to have its own unique set of rules, which enforces better security. Even if one network goes down or gets hacked, the other networks will not be affected.6

Minimise Downtime
The uptime of an organisation is crucial to its profitability regardless of the industry it is in. If a cloud application goes down, businesses will be unable to provide their services to customers or employees. Applications that run slowly also results in a loss of productivity.
SD-WAN minimises downtime by having a strong impact on uptime and application performance. Organisations that utilise it can achieve up to 99.99 percent or greater application availability and superior performance.
As proof, just take a look at MTD Products. The company needed a better way to bring together 6,700 employees across 70 global locations while having to handle 450 network connection points. As the company was constantly expanding, it was not feasible to run efficiently while using its current bandwidth.
Every time a failure occurred, a technician had to come to the data center to reboot the cable modem. This resulted in too much downtime and an unstable network – both crucial to the well-being and productivity of a company. Hence, the company decided to use a full dual-internet SD-WAN solution which saw an increase of over 400% in bandwidth.6
Comparison between companies providing SD-WAN
Let’s take a look at some of the companies that are providing SD-WAN.
As seen from the table, the companies feature and focus on different aspects of SD-WAN. Instead of writing about the different companies, let’s just focus on one of them – VeloCloud.
VeloCloud SD-WAN
VeloCloud, now part of VMware, provides managed IT services such as SD-WAN which is one of the best in the market. It has a scalable, secure cloud network which provides a secure connection through any type of transport. It also comes with a virtual service delivery that can be easily deployed. Depending on the type of service required, these can be delivered either in the cloud or through the private data centre.7
The first factor that businesses should look for if they want to implement SD-WAN should be security. Without strong security measures, important data such as personal particulars can be stolen or hacked. This is devastating for businesses and it is why VeloCloud’s strong security focus is preferable for companies.
Summary
SD-WAN is the next generation of networking solutions which can reduce cost, provide better security and minimise downtime. All businesses should look to implement SD-WAN as it will be beneficial and provides convenience to their company. If you are still unsure or wish to find out more about SD-WAN, you can visit the Netpluz website to find out more either by visiting the website or booking for a free consultation. Alternatively, you may request for an appointment throught submitting your information by clicking here.
Download the SDWAN for Dummies Guide!
Author: Ling Kai Jie
References
- Top 5 Ways SD-WAN Helps Save You Money by Talari Networks, January 09, 2018
https://www.talari.com/blog/top-5-ways-sd-wan-helps-save-you-money/
- These Are the Top 5 SD-WAN Benefits by Atlantech Online
https://www.atlantech.net/blog/these-are-the-top-5-sd-wan-benefits
- 6 Advantages to a Software-Defined WAN Implementation by Technology Solutions That Drive Business
https://biztechmagazine.com/article/2016/12/6-advantages-software-defined-wan-implementation
- SD-WAN’s Benefits Extend Beyond Cost Savings by IT Infrastructure Advice, Discussion, Community – Network Computing
https://www.networkcomputing.com/networking/sd-wans-benefits-extend-beyond-cost-savings
- Four Reasons Why SD-WAN Makes Sense
https://www.sdwanresource.com/articles/419405-four-reasons-why-sd-wan-makes-sense.htm
- 5 Major Enterprise Brands Turning To SD-WAN Technology by Zenlayer April 25, 2019
https://www.zenlayer.com/5-major-enterprise-brands-turning-sd-wan-technology/
- VMware SD-WAN by VeloCloud: Architecture by VeloCloud
https://www.velocloud.com/products/architecture
We live in an interconnected society whereby information and data is readily available at the tip of our fingertips, literally.
You’ve most likely been reading about various cyber-attacks in the news, and have heard about the increasing need for cyber security. But what is cyber security? It is the practice of protecting systems, networks and programs from digital attacks. (Cisco, 2019)
Quite a number companies that Netpluz has contacted have expressed that cyber security is not their greatest concern. Common reasons given are either because they are small companies, and/or don’t keep any data in the cloud. Another reason given is that some companies claim to have very small budgets for IT spending.
But ignorance of the current situation that’s happening is dangerous. And in this article we will provide you with some insights as to why cybersecurity is essential for businesses.
In Singapore, cyber attacks happens more frequently than you think with majority of the attacks aimed towards businesses, online security software vendor Norton has reported that there were 5,430 cybercrime cases in 2017 while the Cyber Security Agency (CSA) detected 23,420 phishing web addresses with a Singapore link.
According to a study by consumer information provider Comparitech, Singapore is ranked 10th best in global cybersecurity. However, despite this, attacks still happen, such as when Singapore experienced its worst cyber attack in June 2018 that resulted in the country’s largest data breach in history. That was when hackers managed to obtain personal particulars of 1.5 million patients. The hackers essentially infiltrated the computers of SingHealth, Singapore’s largest group of healthcare institutions. (Loh, Victor. “The Big Read: As more cyberattacks loom, Singapore has a weak first line of defence.” CNA, 26 February 2019.
With that being said, one should never be complacent despite how safe and secure we may be and never underestimate the importance of cybersecurity in ensuring that your business data is protected.
Here are reasons why your business needs Cybersecurity;
Financial and reputational impact on business
Cyber attacks can have serious implications on your business’ financial situation.
Based on a study done by Ponemon Institute, the average cost of a data breach per compromised record was $148 and it took businesses at least 196 days to detect a breach. This means you’re likely having to bear a heavy price. (Ponemon, Larry. “Ponemon Institute Cost of a Data Breach Study 2018.” SecurityIntelligence, 11 July 2018.
However, it is not just about the financial loss suffered by your business or the cost of recovery; a data breach can also impose reputational damages.
When your business suffers from a cyberattack, your customers will start to lose trust in your business and will start to spend their money elsewhere. This would obviously make it harder for your business to retain existing customers let alone obtaining new ones.
Hence, there’s no need for your business to run on the risk of awaiting for the imminent cyber attack to happen. Instead, take action today to protect your business from cyber attacks and potentially from being wiped out from existence through implementing cyber security measures.
Increasing trend in number of cyber attacks
Criminals can find all sort of methods and entry points into your internal networks through your business’ exposed systems or maybe even your website.
According to the Cyber Security Agency of Singapore (CSA), which is responsible for Singapore’s cybersecurity efforts, the number of cyber attacks, especially ransomware, have increased over the previous years. (Loh, Sherwin. “Singapore sees spike in number of cyberattack-for-ransom cases.” TheBusinessTimes, 10 October 2016. Symantec, an American company that provides cybersecurity software and servcies, also mentioned that financial sector which comprises of financial, insurance and real estates, accounts for 47% of ransomware attacks in Singapore, making it the most vulnerable industry.
This is because ransomware is usually easier to target through a common service, all industries and companies no matter the size, as well as individuals, are targeted.
If you or your business ever encounter a ransomware attack, do not give in to the demands of the cybercriminals because of course, you can’t trust them. Furthermore, paying the ransom doesn’t guarantee that you get back your stolen data or files. It is just a short-term solution but often ends up fuelling these criminal’s confidence in carrying out more attacks at other organisations.
“What makes a good target is outdated security or a poor security posture, resulting in that company or industry being a good target.”
Thus, if you plan to deal with these sort of attacks only after you detected it, you are too late. With highly sophisticated attacks getting common, you need to know that a data breach is bound to happen, especially for small businesses.
Rapid increase in the use of IoT devices
The world we live in today relies heavily on the usage of mobile apps, web apps, and big data. It should come to no surprise that more smart devices nowadays are connected to the internet. These are known as Internet of Things, or IOT for short, devices that are common in homes and offices. Consultancy UK, 2018.
It may seem as though being able to utilise these devices enable many new startups and small businesses to simplify and make tasks more efficient, as well as provides greater control and accessibility.
In reality, that’s not the case.
You see, if the IoT device is not managed properly, it gives cyber criminals a chance to take advantage of it by exploiting the security weaknesses.
For example, people tend to configure their business emails on their personal email, supposedly providing convenience. However, once you step outside the safe zone of your company’s network, you are vulnerable to hackers.
By 2021, it is estimated that there will be 27.1 billion connected devices according to IT services giant Cisco. This means that the problem will only get worse in the long run.
Information, data, and many more can be easily transferred into the wrong hands.
Thus, do not get distracted by the rapid transformation in technology until you forget that protection on these devices should be the priority. Instead, you should conduct regular vulnerability assessments to identify and eliminate the risks.
Increase Productivity
Aside from protecting your business, a well-implemented cyber security measure can maximise your business’ potential output.
According to Computer Economics, it is reported by McAfee that there are over 60,000 known computer viruses currently.This not only means it slows down your computers, but it also forces you to wait to clean the viruses before you can continue working again. Thus, your business is vulnerable to all sorts of viruses and if no action is taken, it can slow down your productivity in work.
Hence, by implementing such effective measures, it will give you the confidence that every aspect of your business is well prepared against potential attacks, contributing to your success. Furtheremore, such confidence gives you the peace of mind, time and resources to focus on other aspects of your business’ growth too.
Save cost
It does not hurt to invest in cybersecurity because in actual fact, it is much more cost-effective as compared to when you suffer a major cyber-attack.
As mentioned, such cyber attacks can cause businesses to lose billions of dollars in terms of reputation loss, loss of sensitive company data, and the consequent cost of compensating the people affected. According to a report by Radware, the average estimated cost of a cyberattack on an enterprise was $1.1 million in 2018, an increase of 52% from the previous year.
However, imagine if your business had just invested a small amount into implementing cyber security measures. The benefits far outweighs the disadvantages.
Thus, implementing these small and cost-effective cyber security measures provides your business a safeguard against these uncertainties.
In conclusion, don’t wait till it’s too late. As mentioned, we should never be too complacent just because we think it won’t happen to us. Your business is at risk financially and reputationally, with the increasing trend in cyber attacks and usage of IoT devices, without cyber security, it can impact your business’ flow. In addition, cyber security also allows for more productivity and cost-effectiveness.
Here at Netpluz Asia, we provide various solutions that can cater to your needs on how you can managed your cyber security. Just watch the video below to find out more!
Author: Amir Matin Bin Abdul Rashid
Reference:
https://www.consultancy.uk/news/18435/five-reasons-cyber-security-is-more-important-than-ever
https://securityintelligence.com/ponemon-cost-of-a-data-breach-2018/
What is Cyber Security?
The name cyber security as straightforward as it sounds is far more important than people usually think. Here are some of the misconceptions that even you may have:
- Only big and important companies or people will fall victim
- Anti-virus and firewall is enough
- Danger can only come from external sources
- Passwords are difficult to crack
- Once a device is infected, users will know immediately
What is cybersecurity and how to prevent cyber-attacks? Cybersecurity is the act of protecting yourself from cyber-attacks online. For cybersecurity to be successful, it has to cover multiple layers of protection spread across networks, programs, computers or data that should be kept safely. How do you make this work in your organisation?
- People – the staff has to be knowledgeable on basic security principles
- Processes – Have a good framework so that the organisation will know what to do In times of cyber attacks
- Technology – New and advancing technologies are used to protect devices
So why implement Cyber Security in your company? I will be listing the top 5 reasons why you should do it for the safety of your company.
Preventing Damage To Company
There are cyber attackers out there who are skilled enough to hack big companies who are already well invested into cybersecurity. Facebook is an example the huge social media company had more than 540,000,000 user records exposed on Amazon’s cloud computing service. Since Facebook has already invested so much in cybersecurity but still gets attacked, it must be pointless for a small company to have cyber security right?
Wrong, not all news are published but there have been cases of companies of all sizes that has been destroyed due to cyber-attacks and it is all because they do not treat cybersecurity with importance. The less invested you are into cyber security means you are prone to more attacks and it could leave much more damage as compared to other companies are more invested. Every day there are more than 4000 hacks made by ransomware alone, this should scare people or companies who think that they are safe from cyber-attacks. With 54% of the firm’s network or data being breached in 2018 it could be your turn any time and the average cost of recovering from a cyber-attack is $5,000,000, will you risk it?
Safekeep Personal Details
In most companies, the database consists of personal details of every staff working for the company. When company data is breached, the hacker has access not only to data relevant to business but the data of the people working for the company. Such data consists of bank accounts, family details, address, etc.
These data can be used as blackmail against the victim and the victim may have to pay a sum of money just to have the data back but it is never guaranteed that the attacker might not have it anymore even after receiving the payment.
Without a cyber-security, the employees, as well as the employer, are in jeopardy of getting their personal information leaked. Hence, for the safety of everyone in a company, cybersecurity should be implemented.
Stay safe from progressing hackers
As technology improves, so does the skills of hackers from all around the world. When big companies such as Facebook, Sony, and Adobe are victims of cyber-attack it shows how smart the hackers can be to get through companies with good encryption. In 2014, South Korea had also been hacked by an employee of Korea Credit Bureau who took credit card details and sold them to credit traders and telemarketing companies. (“TOP 10 of the world’s largest cyberattacks | Outpost 24 blog”, 2019)
With the progress of both Cybersecurity and the skills of hackers, it is important to have an updated and maintained cybersecurity system to reduce the chances of being attacked. With a cybersecurity system that is constantly updated, it decreases the chance of attack as the hackers will have to find a new way to attack the victim due to the updated system blocking them out and being ahead of their capabilities.
Know the different threats
There are many ways for cyber-attacks to happen, the ones that people are more aware of are phishing emails, password hacks etc. however most don’t know about ransomware. What it does is it encrypts business information and can only be unlocked after a large fee is paid. How cybersecurity helps is that a business is able to store their data in multiple places so that they are able back up the data whenever they need to.
Malicious software is constantly improving and so are software security, this is why it is important for a company to maintain their cyber security to prevent such attacks. Having the data kept safe from all the malicious software will ensure that the company does not suffer unnecessary loss of having to recover the data.
It does not require a lot of work
Employing cybersecurity is quite simple, you are able to find some companies who would do the job for you if you employ their cyber security network. They are able to check for viruses, quarantine the virus and also keep you updated on what is happening such as how many attacks, what kind of files are quarantined etc.
As long as you pay the subscription all of these will be done for you and the cost of having cybersecurity will be a lot lesser than when cyber-attacks actually happen to you.
It is evident that cybersecurity is crucial for business to operate smoothly and to reduce cost. It doesn’t take a lot for you to protect yourself from great danger, it is better to be safe than to be sorry so make the right decision or bear with the consequences.
Author: Tan Ming Rui, Aloysius
References:
Why is Cyber Security Important in 2019? – SecurityFirstCorp.com. (2019). Retrieved from https://securityfirstcorp.com/why-is-cyber-security-important/
Services, P. (2019). What Is Cybersecurity?. Retrieved from https://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html
Bordoni, S. (2019). The importance of maintaining cyber security in your business. Retrieved from https://www.itproportal.com/features/the-importance-of-maintaining-cyber-security-in-your-business/
(2019). Retrieved from
https://www.quora.com/What-is-cyber-security-Why-is-it-important
Five reasons cyber security is more important than ever. (2019). Retrieved from https://www.consultancy.uk/news/18435/five-reasons-cyber-security-is-more-important-than-ever
https://www.pexels.com/search/cyber%20security/
TOP 10 of the world’s largest cyberattacks | Outpost 24 blog. (2019). Retrieved from https://outpost24.com/blog/top-10-of-the-world-biggest-cyberattacks
Does internet work differently for businesses? Isn’t it the same as using the normal internet? Most people think it is but the answer is NO! Business internet is not just internet. In fact, the internet only makes up a branch of Business Internet.
How does business benefit from internet?
Business internet refers to how businesses use the internet to enhance the operation of their daily business. It provides both connection and connectivity for business owners to interact with each other even at long distance. Read on to find out why businesses need to know about the features of the 4 internet grades.
4 reasons to prove that Business Internet is more than just the internet.
Moving on, this article will further explore the benefits of the 4 internet grades. Business internet is made up of 4 different grades, namely Fibre broadband, GPON, Ethernet and Metro Ethernet.
1) Fibre Broadband
Fibre broadband utilises fibre optic cable that allows the transferring of data from 1 location to another in a short period of time. Fibre broadband may sound familiar to many people as it is commonly used in homes and businesses. For example, SingTel provides fibre broadband service for customers to achieve stable internet connection even at a largely exposed area. This makes it ideal also for businesses that need wide coverage.
There are several benefits of fibre broadband such as speed, strength of connectivity and latency.
- Speed
Fibre broadband is able to provide an ultra-high-speed of up to 500Mbps which enables efficiency of business operations and large data transfers that are dependent on the internet.
- Strength of connection
Strength of connection refers to the ability to have a reliable connection regardless of location in the premises, which enables smoother processes at work.
- Latency
Latency refers to delays that occur when processing data over the internet. Fibre-optic Internet helps to decrease latency issues that users may experience on cable Internet, especially when downloading, uploading of high-definition files.
2) GPON
GPON is Gigabit Passive Optical Network for short. One of GPON functions is being able to transmit Ethernet to the desired area. In addition, it is also a robust device that allows users to achieve high-speed internet connections. GPON provides the ability to combine several services onto a single fibre transport network. The benefits of using GPON include minimising cost for the infrastructure with increased and better bandwidth.
- Cost
GPON utilises passive optical splitter which covers the connection to desired areas without making use of more than one device for a large area. This results in lower costs with up to 1Gbps speed. Thus, having 1 GPON in a room is sufficient to provide stable connection for users especially for businesses with many employees.
- Infrastructure
GPON system includes an optical line terminal (OLT) that connects several optical network terminals (ONTs) together using a passive optical distribution network (ODN). It takes up lesser space to place the devices.
- Bandwidth
GPON offers an increased bandwidth at a low cost. It provides a service coverage of up to 20km that is also capable to overcome any obstacle such as twisted pair cables and decreased network nodes.
3) Ethernet
Ethernet refers to connecting computers together to a local area network or LAN. Ethernet is more common to people as it is was one of the first few traditional inventions that eased the process of providing a connection for people to use. Yet it still has many benefits for today’s business environment, including providing reliable, secure and energy efficient connectivity. For example, Ethernet actually provides faster connection as compared to Wi-Fi. This is due to its use of cables that connect to a particular TV, computer, etc.
Find out more: Watch to find out how does Ethernet work?
- Reliability
When properly set up, Ethernet provides reliable connections to devices without disrupting the user experience. It transmits connections almost immediately at speeds of up to 10 Gbps when using cabled Ethernet.
- Security
Ethernet also guarantees security as it makes it harder for the system/connection to be hacked. When users use Ethernet for their wired network, the only way for intruders to have access to the connection is by physically plugging their device to the main router which is harder to do without getting caught!
- Energy efficient
Lastly, Ethernet is a good source of connection as it utilises energy efficiently. The use of cables consumes less energy as compared to using Wi-Fi connections. This is because Ethernet has a network cable called Category 6 (Cat6) which is used as an infrastructure for network. The Cat6 cable comes in different lengths up to 100m. As a result, users enjoy greater mobility than if using shorter cables while still experiencing increased performance of up to 250 MHz.
4) Metro Ethernet
Metro Ethernet which is also referred to as Metropolitan area network, allows connectivity for a large group of users with an extended internet coverage. Many businesses use Metro Ethernet because it serves several functions such as connecting residential businesses/subscribers to the internet, allow multicast delivery which is essential for video conferencing, etc. Hence, this will greatly benefit users with improved scalability, quality of service and ease to use.
- Scalability
Metro Ethernet is compatible for speed connection that is up to 1Gbps. Users are given the choice to increase bandwidth without having to purchase or install any new equipment.
- Quality of service
Quality of service is guaranteed when using Metro Ethernet as it has a reliable Ethernet operation that is able to detect any connection failures that is experienced by users. To add on, it also supports features of the business environment such as transferring of data.
- Easy to use
Metro Ethernet make use of networks that are less complex to set up as it has a few equipment needed only. It is also easier to deal with, to maintain the network connection. As a result, it also reduces cost of equipment and ownership.
In addition, a case study done by Cisco, a well known technology company found out that the use of Metro Ethernet positively impacts businesses. Cisco has published a case study demonstrating the suitability and benefits to businesses in technical terms.
Summary
There are various articles that have been written to create awareness on the use of the various grades of business internet.
For example, SingTel, the largest mobile network provider in Singapore, also recommended business to opt for Metro Ethernet. SingTel provided a list of features that Metro Ethernet have to offer and also the benefits. It also further elaborates the types of businesses that will benefit from using Metro Ethernet. For example, for those who require a strong and committed connection to Data Centre or Cloud.
In another article, Megapath, a fusion company, supports the adoption by businesses of Ethernet. To add on, many companies/offices are still using Ethernet to provide connection as they feel that it fits their business environment.
To sum it all up, there are advantages and disadvantages when using the various grades of internet available. Depending on the nature of the business and connectivity required, there is definitely a particular internet grade that would be suitable.
You can read more on the internet grades by visiting the Netpluz website! It is a transforming Managed Communications Service Provider that helps client become more agile by simplifying their Information and Communications Technology (ICT) needs. It started in 2015 and provide a variety of IT solutions for business such as Data, Voice, Video, Mobility, Analytics and Cyber Security.
Author: Nurul Aishah Binte Khuzairi
References
· Fibre Optic Broadband Explained | MoneySuperMarket
https://www.moneysupermarket.com/broadband/fibre-optic-broadband-guide
· 11 Huge Business Benefits of Fibre Internet Connectivity
https://www.atlantech.net/blog/11-huge-business-benefits-of-fiber-internet-connectivity
· What is Metro Ethernet? | Juniper Networks
https://www.juniper.net/us/en/products-services/what-is/metro-ethernet/
· 11 Huge Business Benefits of Fibre Internet Connectivity
https://www.atlantech.net/blog/11-huge-business-benefits-of-fiber-internet-connectivity
· Benefits of the Ethernet Cable: Why You Should Be Plugging …
· Point to Point vs. GPON Fibre Internet | iTel Networks
https://itel.com/p2p-vs-gpon-fiber/
- Ethernet or GPON: Which technology is best suited for Information Transportation Systems (ITS) of the 21st Century?
· Metro Ethernet over GPON enhances business services .
- MetroEthernet – singtel.com
https://www.singtel.com/business/products-services/connectivity/domestic/ethernet/metroethernet
· GPON Technology Overview and Benefits – ctscabling.com
https://ctscabling.com/blog/gpon-technology-overview-benefits/#.XRqzOugzaM8
· Metro Ethernet – Business Benefits – telcosolutions.net
https://www.telcosolutions.net/post/metro-ethernet-business-benefits
Business internet. Not many people truly understand what it means, whereas others would just assume that it simply refers to “Internet connection”, or “Firewall”. But did you know that there is so much more to the meaning of Internet, especially when used by businesses.
From 1994 to 2000, there was the dot com bubble in the US, whereby there was a huge internet crash that resulted in a huge fluctuation in the price of goods on the internet. According to Chron, the internet continued to be a huge profitable tool for businesses as a means to market their organisation and products. There are actually many building blocks that forms the internet that businesses use on a daily basis such as Fibre Broadband, GPON, Ethernet, Metro Ethernet. Each of these internet grades would form “Business Internet” and here are some of the reasons why these building blocks would help benefit your organisation.

Fibre Broadband
Fibre Broadband is a connection that uses fibre optics to deliver data to businesses and homes. In April 2019, SP Telecom announced that it was investing “hundreds of millions” of dollars over the next five years to build an alternative to the government-backed Next Generation Nationwide Broadband Network (NGNBN).” This shows that the Singapore government understands the importance and benefits of Fibre Broadband. So you may ask, how is fibre broadband different from standard broadband? Well, it’s fairly simple and straightforward. Standard broadband uses copper wires for data transfer, whereas Fibre Broadband uses fibre optics which is much faster. Here are some benefits of Fibre Broadband according to Atlantech:
Speed
Fibre broadband speed (which ranges from 5 Mbps to 100Gbps) is many times faster than the normal internet connection, so much so that even during times when there is high usage of internet access, you wouldn’t notice any difference in internet speed! Furthermore, research conducted by Sandisk has shown that slow internet connections cost employees “one week per year of productivity.”
Latency
Latency refers to the delays that occur while processing data over an internet connection. Hence with fibre broadband, you get to enjoy
- Downloading and uploading of large sizes of data
- No interruption on international calls that require an internet connection
- Security
With fibre broadband, you can protect your data anywhere as did you know, the only way to steal information through fibre optics is to manually cut the wires that is linked to the database!
GPON
GPON, which stands for Gigabyte Passive Optical Network refers to networks that rely on optical cables to transmit and deliver information. A GPON network consists of 2 transmission equipment, which are Optical Line Termination (OLT) & Optical Network Unit (ONU). What GPON does is that it uses splitters from the network provider’s central location to “split” the network to multiple users. You might be wondering why your business might need GPON. Well nowadays, many internet service providers require a longer transmission reach, higher reliability and bandwidth. Hence, GPON is able to meet these requirements by using the OLT and ONU to
- Longer transmission distance: Covers up to 60km coverage radius
- Higher Bandwidth: GPON could be able to support the maximum transmission
In fact, GPON is getting so successful that Cisco, a multinational technology company has announced a GPON system that is part of their plan for implementing “Access Networking”. To read more about their new developments, click here.
Furthermore, GPON gives users the ability to consolidate multiple servers into a single transport network, which is the perfect solution for businesses with multiple points. Hence, instead of using separate servers which could be separated geographically, businesses could use GPON to consolidate all these servers to ensure the smoother transmission of data and the overall increase in productivity.
Ethernet
What exactly is Ethernet? As explained by LiveWire, Ethernet simply refers to technology that is commonly used in Local Area Networks (LAN), which refer to a network of electronic devices that cover a small area such as an office or your house! In fact, you are probably using Ethernet every day without even realising it! According to The Chartered Institute for IT, many network providers across the globe are looking to utilise Ethernet in their businesses to reap the benefits that come along with it.
Why should you use Ethernet as compared to your normal Wi-Fi? It’s fairly simple. For starters, the maximum speed of a typical Wi-Fi connection is 866.7Mb/s, whilst an Ethernet connection could offer up to 10Gb/s. Furthermore, as compared to Wi-Fi, which is prone to hacks as it is not entirely secure, Ethernet is much safer as all the data is transmitted through the cables that are connecting all the electronic devices together, hence the only way to actually “hack” an Ethernet connection is to physically plug the device into your router!
Therefore, switching our office or home internet connection from Wi-Fi to Ethernet would be highly recommended! For more benefits about Ethernet, you can refer to this Link to find out more!
Metro Ethernet
Metro Ethernet is basically an Ethernet technology network that covers a metropolitan area. It is mainly used for connectivity to public internet, or connectivity between businesses that are geographically located separately. The difference between metro Ethernet and Ethernet is that metro Ethernet caters towards a much bigger area, as suggested in the word “Metro”.

Benefits
- Flexibility—Supports a wide variety of services and transports.
- Reliability—Ethernet operations, administration, and maintenance (OAM) performs path discovery, detects and reports connection failures, and measures performance.
- Cost-Effectiveness/Ease of Use— The network is much easier to maintain and use, which would, in turn, lower ownership, manpower and equipment cost.
- Quality of Service (QoS)—Supports QoS features, such as classification, marking, policing, queuing, and scheduling.
- Scalability— Metro Ethernet is able to support internet speeds ranging from 1 Mbps to 10 Gbps, and it could be done without any prior instalment or purchase.
If you would like to find out more about the features, further benefits and cloud exchange networks, here’s the Link!
In Conclusion, these 4 main building blocks make up the “Business Internet” that you experience on a daily basis, whether you are at home or in your office. Understanding the benefits of GPON, Fibre Broadband, Ethernet as well as Metro Ethernet could help boost productivity in the workplace, as well as ensuring that your database is secured 24/7.
If you are looking for a company that is able to cater to all your technological needs and provide you with the benefits of “Business Internet” mentioned throughout this blog, then find out more at Netpluz.
Author: Tristan Oh Jiaxuan
References:
Netpluz Internet Connectivity for Business | Secure & Reliable Internet
https://www.netpluz.asia/services/data/managed-internet/
11 Huge Business Benefits of Fibre Internet Connectivity
https://www.atlantech.net/blog/11-huge-business-benefits-of-fibre-internet-connectivity/
What is GPON?
https://www.router-switch.com/faq/what-is-gpon.html
Ethernet LAN Explained
https://www.lifewire.com/what-is-ethernet-3426740
Insights from CableWholesale
https://www.cablewholesale.com/blog/index.php/2016/06/07/benefits-of-the-ethernet-cable-why-you-should-be-plugging-in/
What is Metro Ethernet? | Juniper Networks
https://www.juniper.net/us/en/products-services/what-is/metro-ethernet/
What is GPON (Gigabit Passive Optical Networks)? | Carritech Telecommunications
http://www.carritech.com/news/gpon-gigabit-passive-optical-networks/
What Are the Benefits of the Internet to Business?
https://smallbusiness.chron.com/benefits-internet-business-316.html
WIFI MOBILITY
Benefit of Wi-Fi Mobility for Office Purpose
Having wireless interconnectivity is one of the requirements for business to stand out nowadays, as more and more people connected to digital world to find for information. Having wifi installed in office has proved to benefit the business owner and their employee when working on daily basis for their mobility.
Based on the study conducted by The Economist Intelligence Unit (IEU,) it’s known that having wifi installed in office will have a positive effect on both business owner and their employee on their mobility. The study said that workers with high mobility and use their mobile technology well are typically more productive, creative, satisfied and loyal.
The 1,865 employees surveyed by IEU found that organizations that rated as pioneers with respect to mobile enablement saw 16 percent boost in their productivity, 18 percent increases in creativity, 23 percent more satisfy, and 21 percent become more loyal when compared to companies or other organizations that ranked poorly with respect to supporting mobile technology.
Mobility Within the Office
Having Wi-Fi installed in office is one way an organization can support the mobility of their employee to progress and engaged more with them. Wi-Fi in office is great for convenience as it will allow employee to work and access network resources from anywhere. For example, employee can work and access information when they are in a meeting room or any part of place in office aside from their own cubicle.
Increase Employee Productivity
When company support mobile enablement and their employee’s mobility, employee become more productive because they will focus more on the assigned task regardless the location. When employee can connect to internet anywhere within the office, they can collaborate and engaged more quickly in real time. Thus, it will reduce any delays and increase more on their productivity while working.
Simpler Infrastructure
When office support wireless connection, it’s simpler to organize the office layout and desk location for the employee. This become easier as the office layout won’t be dictated by the cables and wires installation that sometimes is expensive to purchase and maintain overtime.
More insight through Wi-Fi Analytics in Office
Nowadays Wi-Fi is getting better with their analytics feature, such as tracking device based on location. Having such Wi-Fi installed in office, could help to conduct data and more insight about your employee for better strategic planning when designing office layout, employee attendance or to locate employee during emergency if they are still within the office or building in the event of evacuation.
Source :
https://www.networkworld.com/article/3062058/mobile-wireless/a-mobile-first-strategy-improves-employee-productivity-study-finds.html
https://www.arubanetworks.com/assets/EIUStudy.pdf
Prevention is Always Better than Cure
Understanding why being proactive is always the best solution to fight an attack.
The cost of protection is rather small compared to the cost of regret when the company’s reputation jeopardized after DDoS Attack. Companies that are targeted by Distributed Denial of Service (DDoS) attacks are not only financially disadvantaged, but their image becomes polluted as well.
Moving in line with our national plan to become a leading digital economy requires us to digitize and have a strong online presence. Having a good online presence is essential for the long-term growth of any business and it’s also the good way to find potential customers and gain the trust of existing ones.
But as we go more digital than ever, cyber threats and attacks are almost inevitable. Cyber Security Agency of Singapore (CSA) reported that there are 5430 cybercrime cases back in 2017. From previous year, the cybersecurity cases growing from 15.6 percent to 16.6 percent.
Distributed Denial-of-Service (DDoS) attack is the malicious attempt to disrupt normal traffic by sending floods of internet traffic to targeted server, service or network. This attempt can slow down your server and could take your whole online services down. The reason of the attack is varied, could be business’ competition, revenge or part of hacktivism.
Having managed DDoS Protection towards the attacks will be the best proactive solution that any business should do. This proactive solution might help your company to mitigate the good and bad traffic that enter your company website, applications, and network infrastructures from DDoS attacks and hacking.
While the number of attacks increase in time, many of business still haven’t really understand to react well to the phenomenon. Study conducted by reputable cyber security company found out that at least 34% business still don’t use any protection toward DDoS and only rely on their ISP to shield them from attacks. The study also found out that 30% of the businesses that actively use DDoS protection only use it because they were a victim of DDoS in the past while the rest 35% use DDoS protection because they are required to do so for regulatory purposes.
The best solutions to deal with DDoS are knowing the risk of DDoS and to have the better understanding of the attacks, having the prevention and response plan to it. Thus, it’s always suggested by all IT experts that the best defense that business owner can do is to have themselves protected since the beginning, rather than must deal with bad publicity after becoming another victim of the cyber-attacks.
Source :
https://www.kaspersky.com/about/press-releases/2018_ineffective-ddos-strategies
https://www.csa.gov.sg/~/media/csa/documents/publications/singaporecyberlandscape2017.pdf
https://www.imda.gov.sg/sgdigital/digital-economy-framework-for-action
Understanding Customer and Employee Behavior Using Wi-Fi Analytics
Nowadays, staying connected anywhere, all the time is a basic need for everyone. Installing free Wi-Fi as a value-added service for guest and employee can enhance their user experience with your company, the service you offer or the business you are trying to build. Based on IMDA Report, Wireless Broadband Subscriptions reached 11,300,200 in total in November 2018, this number includes all retail broadband Internet access subscriptions and Wi-Fi hotspots.
The need to stay connected can be an opportunity for any business to gain more information about both customers and employee. Wi-Fi analytics will benefit business by providing information about the user’s location that can be leveraged for advanced analytics to enhance performance and stay on the competitive edge.
Wi-Fi analytics works by detecting any connected device, such as a mobile phone, laptop or tablet if they have Wi-Fi enabled on. The technology on Wi-Fi analytics helps to capture data such as location point, the timestamp from the device. These data can be useful to give you the visualization of the location heatmap, the route they take, how much time they spend on certain area and number of new visitor or repeater.
In retail industry, having Wi-Fi analytics installed will be useful to find out how exactly your customer moves through a venue, where do they stop and linger, where is the spot they decide to keep moving, are you getting a lot of repeat customer or new customer and are the staffing levels appropriate at all times and in all places. Having these data on how customers are using a space could help retailers to optimize better layout for their shop and identify the best locations for their product to increase more sales.
Wi-Fi analytics could support location-based advertising and information and help to navigate the user to go to a certain spot with indoor navigation and track personnel locations real-time. In the healthcare industry, Wi-Fi can help employee and visitor to find their way through complex facilities. This can help them to save more time during an emergency.
In an office, Wi-Fi analytics can be a location tracking device as you can check the history of your employee’s movement and better identify their location during a critical time, such as an emergency. Thus, this device can also be useful to track your employee in the real-time. Not only employee attendance, but it can also help to track high-value assets to minimize inventory loss by configuring alerts for when devices enter or leave a location to reduce theft and loss.
These benefits of Wi-Fi analytics not only enhance both customer and employee experience but also can help the business to look for a new opportunity, engaged with the user, and make a profitable decision that could drive the business revenue.
Source:
https://www.ruckuswireless.com/rucktionary-categories/location-and-analytics
How To Be Cyber-Prepared After SingHealth Recent Database Attack
Health Minister Gan Kim Yong and Minister for Communications and Information S. Iswaran both described recent SingHealth’s attack was the most serious personal data breach in Singapore’s history (Tham, 2018).
Reported by Channel News Asia, it is known that personal data of 1.5 million patients who visited SingHealth’s clinics or polyclinics between May 1, 2015 to July 4, 2018 were copied and 160,000 of their medical records accessed before the database admin detected the unusual activity (Kwang, 2018).
On July 10, Integrated Health Information System (IHiS) confirmed that data had been stolen between June 27 to July 4, 2018. Cyber Security Agency of Singapore (CSA) established the fact that the attackers first gained access through a breach on a particular front-end workstation and from there, they managed to get credentials to access the database. This accident shows us that no one can really escape the threat of cyberattack. We all have the same potential to become victims of cyberattack as the IT landscape is always evolving and what organizations should do today is to be more proactive in building up their own network and cybersecurity resilience.
Minister for Communications and Information, S. Iswaran on SingHealth cyberattack said that we cannot allow and must not allow this incident or any others like it to derail our plans for a Smart Nation (Yong & Tham, 2018).
“We must adapt ourselves to operate effectively, and securely in the digital age. So that we can deliver better public services, enhance the economic competitiveness and create jobs and opportunities for Singaporeans,” added S. Iswaran on the news conference.
A data breach is a serious issue everywhere. This accident could be a nightmare in daylight for a business owner. Because when your security is compromised, this could cripple your business, costing you thousands or millions of dollars and having bad exposure to your brand image and reputation.
The next question is that what we should do to prevent this thing from happening again?
The key to deal with cyberattacks is not the chance or warranty that they won’t attack you in the first place and try to get into your system. The key is to be prepared when they do try to attack you. When you build up your network and cybersecurity resilience through the adoption of cybersecurity tools or services to mitigate such threats, on different levels, for example, ISP level, Network / Server and End Points, you can respond quickly and effectively when the attacker is trying to attack your system.
What are the best solution that our Cyber Security experts here at Netpluz can offer you to be cyber-ready after learning from the recent SingHealth’s database server attack?
The 4 Levels of End-to-end Cyber Security Protection by Netpluz
ISP Level Network Defense
- DDoS Mitigation and Web Application Firewall (WAF)
- DDoS Mitigation (Internet Clean Pipe) – A total solution to protect your company’s infrastructure from malicious traffic and DDoS attacks. More specifically, Netpluz Internet Clean Pipe, powered by Nexusguard, prevents flooding or volumetric attacks that abuse the weaknesses in various communications protocols, including TCP, UDP, ICMP, FTP, and SIP.
- Web Application Firewall (WAF) – this can protect a server from cross-site scripting, SQL injection attacks. By preventing the injection of SQL queries, the WAF can help keep sensitive information stored on the database away from snooping eyes.
On Premise Network Perimeter Defense
- Firewall – All the advanced networking, protection, user, and app controls you need to stay secure and compliant.
On Premise Server Perimeter Defense
- Server Protection Software installed on the server – to help prevent an attacker from taking advantage of the common hacking techniques and persistent hacking attempts. Netpluz recommends SOPHOS Server Advanced Protect.
End-point Protection
- Endpoint protection – For those who have access to the database server- end-user machines. This is to help detection of malware be installed on the machines that can potentially gather information on what users are accessing (ie. Database server). Also, to prevent ransomware to spread across the network. Netpluz recommends SOPHOS Advanced Protection + Intercept X.
Some Useful Tips & Tools :
- Email Phishing Simulation Tool– To educate and create security awareness to the largest attack surface – the end-users, on what a phishing email looks like and be trained to spot a legit email and URL links. People are the #1 weakness, from a security perspective, in any organisation.
- Keep Patches updated– make sure all software’s are up-to-date and security patches too, this is to fix those known vulnerabilities that can be exploited by attackers.
- Do not use shared server – if your database store sensitive data, you should have your own dedicated server instead of getting a hosting provider to host your data. You can opt to do it but make sure you review with the hosting provider their security policies and what will be their responsibilities in the event that your data been compromised.
Source :
- Kwang, Kevin. (2018, July 20). News. Singapore health system hit by ‘most serious breach of personal data’ in cyberattack; PM Lee’s data targeted. Retrieved July 24, 2018 from https://www.channelnewsasia.com/news/singapore/singhealth-health-system-hit-serious-cyberattack-pm-lee-target-10548318
- Yong, Jeremy Au & Tham, Irene. (2018, July 21). Info on 1.5m SingHealth Patients Stolen In Worst Cyber Attack.Retrieved July 24, 2018 from https://www.straitstimes.com/singapore/info-on-15m-singhealth-patients-stolen-in-worst-cyber-attack
- Tham, Irene. (2018, July 20). Personal Info of 1.5m SingHealth Patients, Including PM Lee, Stolen In Singapore’s Worst cyberattack. Retrieved July 26, 2018 from https://www.straitstimes.com/singapore/personal-info-of-15m-singhealth-patients-including-pm-lee-stolen-in-singapores-most